It’s a jungle out there. And by ‘out there,’ I mean in the online world, where scams, data breaches, and outright thievery are depressing facts of life. While many of us with a reasonable technical background might easily spot the markers of an online attack, our loved ones – friends, parents, or even siblings – might be just one click away from getting fleeced by a bad actor.
But here’s the good news: you can be their digital hero! You can help your family get smarter and less likely to fall victim to these scam artists. It doesn’t require complex coding or deep technical expertise, just a few heart-to-heart conversations, perhaps during a family Zoom call, a casual picnic, or even over the holidays. All it takes is a few minutes of real talk to empower them.
This isn’t about shaming or making anyone feel inadequate. It’s about digital caregiving, breaking down cybersecurity into manageable, actionable steps that even the most non-technical family members can grasp and apply in their daily lives. Think of it as teaching essential cyber hygiene, just like we teach personal hygiene, to keep their digital footprint clean, safe, and secure. Let’s dive into some simple habits that can make all the difference.

1. **Foster a Culture of Healthy Suspicion**I always start with this crucial point because, at its core, it challenges a fundamental aspect of our social experience. Unless you were raised by wolves, you probably learned early to be polite and cooperative with other people, especially authority figures. The most common forms of online mischief take advantage of this very human trait, using social engineering to dupe trustworthy souls into giving up information they really shouldn’t.
It’s a tough pill to swallow, but the internet is absolutely filled with grifters, thieves, and ne’er-do-wells who don’t deserve your trust. Encouraging a bit of healthy suspicion is a great way to get the conversation started. It’s about empowering your family to question unsolicited requests and messages, rather than blindly trusting them because they appear legitimate or urgent.
One of the best ways to bring this concept to life is with a few real examples. I keep a folder filled with examples of phishing emails, fake invoices, and other scams I’ve received. Walking through some of those examples helps to show what the scamsters were trying to accomplish, and what specific red flags to look for. This practical demonstration can be incredibly effective in helping non-tech users understand why a trusting nature can expose them to seemingly legitimate emails, texts, or phone calls.
Many non-tech users are vulnerable precisely because of their unfamiliarity with verifying website URLs or spotting phishing attempts. By showing them concrete examples of deceptive emails and texts, you can help them develop an instinct for what looks “off.” This isn’t about being paranoid; it’s about being prepared and knowing that it’s okay, even necessary, to be suspicious of anything that feels even slightly amiss in the digital world.
Read more about: From Budding Beginnings to Bright Futures: 14 Core Childhood Realities That Pave the Way to Adulthood

2. **Understand the Stakes: “What’s the Worst That Can Happen?”**This question is one of my favorites to ask because it immediately helps emphasize just how much we all have to lose if someone successfully takes over an important online account. Cybersecurity isn’t some abstract concept; it has very real, tangible consequences. Sometimes, painting a vivid picture of these potential outcomes can be the most effective way to convey its importance.
Scenarios help immensely here. Imagine someone gaining access to your online banking account and starting to transfer money around. Or what if a hacker broke into your Google Drive account and deleted all your precious photos, years of memories, in an instant? What if someone got hold of your credit card information and went on a fraudulent shopping spree, leaving you to deal with the aftermath?
In some dire cases, those losses would be irreversible, like the deletion of irreplaceable digital memories. In others, while the damage might eventually be undone, reversing fraudulent charges and rectifying the situation could take days, weeks, or even months of frustrating effort. These aren’t just minor inconveniences; they can lead to significant financial losses, crypto theft, blackmail, and even coercion.
Telling these kinds of stories – even hypothetical ones – helps emphasize that digital security isn’t something to take lightly. It underscores the potential for catastrophic damage if critical accounts are compromised. Understanding the magnitude of what’s at stake transforms cybersecurity from a tedious chore into a vital act of self-preservation and family protection.
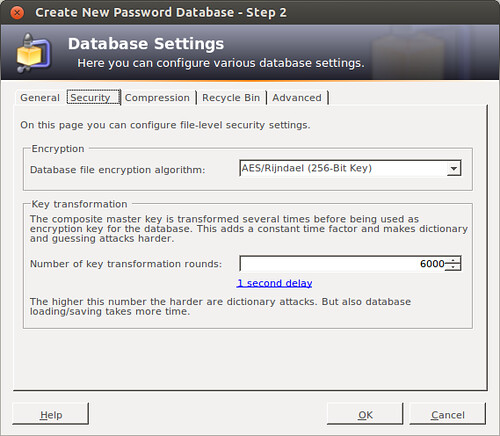
3. **Embrace Password Managers**For many, the idea of managing multiple, complex passwords feels like an impossible task. That’s where password managers come in as an absolute game-changer. My advice? Set up an account for your family members using whatever password manager you think they’re best equipped to use. Are they deeply embedded in the Apple ecosystem? Great, then Apple’s iCloud password manager might be a natural fit for them.
Consider adding them to a family account for your preferred password manager, such as 1Password or Dashlane, if you already subscribe to one. This can not only save them a few bucks but also provide a seamless way for you to train them in how the applications work across all their devices – be it their PC, Mac, or smartphone. The goal is to make the transition as smooth and painless as possible.
The real point here is to convince them to stop typing passwords manually and, more importantly, to stop trying to remember them all. Instead, they should start using a modern tool that can automatically generate, store, and fill in complex, unique credentials for them. A password manager significantly simplifies things by removing the burden of memorization, which is often cited as a major hurdle to good password hygiene.
These tools are designed to keep them more secure by ensuring every account has a unique, strong password without any effort on their part. Once they experience the convenience and security a password manager provides, they’ll wonder how they ever managed without it. It’s a fundamental step towards fortifying their digital life and one of the best investments of time you can make.
Read more about: Fortify Your Finances: 15 Essential Items You Must Remove from Your Wallet to Prevent Identity Theft
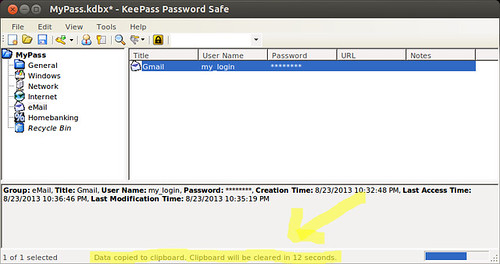
4. **Practice Strong, Unique Passwords & Avoid Reuse**This conversation can sometimes feel a bit awkward, but it’s absolutely crucial. Let’s be honest, most people have a favorite word, phrase, name, or date that they think of as ‘my password.’ When prompted to create a new online account, they might instinctively type something like ‘Rover1473,’ because that was the name of their beloved first dog and the number of their childhood home. This is where we need to intervene with some tough love.
This is the pivotal moment where you have to talk about two non-negotiable rules for digital safety. First, explain the immense danger of reusing passwords across multiple accounts. If a bad actor gains access to just one of those accounts through a data breach, they can then use that same username and password combination to potentially unlock dozens of other services your family member uses, leading to catastrophic damage. This is often referred to as ‘password recycling,’ and it’s a critical vulnerability.
Second, emphasize the absolute importance of creating unique, random passwords that are impossible to guess. Passwords are like toothbrushes: you never share them, you have to change them regularly, and you shouldn’t use the same one for everything. Encourage them to use passphrases instead of simple words, as they are significantly more difficult to crack. For instance, ‘IloveDogs2025!’ is far more robust than ‘password123.’ The longer the password, and the more it mixes letters, numbers, and symbols, the stronger it becomes. Aim for at least 12 characters and avoid obvious information like birthdays or pet names.
While you probably can’t convince them to change every single password right then and there, you can do the next best thing. Use that brand-new password manager you just set up to find one of those weak, reused passwords. Then, walk them through the process of changing it into a good, strong alternative. This hands-on experience not only solidifies the lesson but also demonstrates the practical application of their new security tool, making it less daunting and more achievable.
Read more about: Fortify Your Digital Fortress: 14 Proactive Strategies to Shield Your Identity from Scammers

5. **Prioritize Critical Account Security**Not all online accounts are created equal, and this can be an incredibly enlightening conversation to have with your family. It’s vital to ensure they understand that some sites and services are dramatically more important than others in terms of the potential damage if compromised. Identifying these ‘crown jewel’ accounts is a key step in focusing security efforts where they matter most.
Think about it: their primary email account, their online bank account, credentials for crucial services like the IRS and Social Security, and even their social media profiles. These are not just casual logins. These are the gateways to their financial well-being, personal identity, and digital footprint. If any of these are compromised, they can open the door to truly catastrophic damage, from identity theft to complete financial ruin.
So, here’s a highly actionable tip: just to get started, make a list together of the 10 most important websites they use. Once identified, dedicate time to changing the passwords for all of these critical accounts. Immediately save these new, strong, and unique passwords in their brand-new password manager. Then, walk them through the process of signing in on their favorite platforms – whether it’s their PC, Mac, or smartphone – to ensure they’re comfortable with the new system.
By taking these focused steps, you’re not just changing passwords; you’re implementing a foundational layer of security for their most vulnerable points. Make sure they understand what a huge step they’ve just taken. This targeted approach prioritizes their most valuable digital assets, providing a significant boost to their overall cybersecurity posture and peace of mind.
Read more about: Unlocking Peace of Mind: 14 Top Apps to Discreetly Track Your Family’s Location for Ultimate Safety

6. **Stay Updated: “Things Change…”**Some people, particularly those who are technically challenged, often rely on very specific, step-by-step instructions for common digital activities, perhaps even a Post-It note stuck to their monitor. The problem with this approach is that security providers and website managers are constantly tweaking their user experience, introducing new steps, changing wording, or redesigning interfaces. This can instantly make static instructions obsolete, leading to confusion and frustration.
Instead of just teaching the ‘how,’ it’s crucial to ensure your audience understands the ‘why’ behind security practices. Little things on a screen might change, but if they grasp the underlying goal – for instance, why an update is important – they can adapt to minor interface variations. This empowers them to think critically and navigate new situations without constant hand-holding, which is a hallmark of digital resilience.
One of the most vital ‘whys’ involves software updates. Think of updating software like getting a flu shot: you might not see the immediate benefit, but it’s crucial for protection. More often than not, these updates aren’t just about adding shiny new features to apps or devices; they are absolutely critical for patching vulnerabilities that hackers can exploit. These patches close security loopholes that threat actors are constantly looking for.
To make this habit effortless, encourage family members to enable automatic updates wherever possible. This includes for their operating systems (Windows, macOS, Android, iOS), antivirus software (like Bitdefender Ultimate Security or Mobile Security), and even their browsers and other frequently used apps. Regular updates are a simple yet incredibly effective way to keep devices protected against the latest cyber threats, ensuring their digital immune system is always at its strongest. Without these updates, even the best initial security setup can quickly become outdated and vulnerable to attack.

7. **Enable Multi-Factor Authentication (MFA) Everywhere Possible**We’ve mastered strong passwords and embraced password managers, but it’s time to layer up our security. Imagine a digital superhero sidekick, adding a crucial extra shield to your most important accounts. That, my friends, is Multi-Factor Authentication (MFA), making unauthorized access exponentially tougher.
Here’s the deal: even if a sneaky hacker snatches your password (your “key”), they’ll still be locked out without that second verification piece. This could be a code to your phone, a fingerprint scan, or a tap on a trusted device. It’s like needing both a key *and* a secret handshake to get into your digital spaces – simple, yet incredibly powerful.
This isn’t just about a little extra safety; it’s about *significant* protection for accounts holding financial information, precious memories, or identity. For banking, primary email, or social media, MFA is non-negotiable. Enabling it proactively saves immense headaches, potential financial ruin, and irreversible data loss.
Most major online services offer MFA. You’ll typically find the option in your account’s security settings. Walk your family through turning it on for critical services. Show them how the verification code arrives, ensuring they’re comfortable wielding this powerful new shield for their digital lives.

8. **Think Twice Before You Click: Spotting Phishing and Scams**We’ve cultivated healthy suspicion, now apply it to a pervasive threat: phishing and scams. These aren’t just spam; they’re meticulously crafted deceptions designed to exploit trust and urgency, tricking users into clicking malicious links or divulging sensitive info. Dodging these traps requires a keen eye for red flags.
Teach your family to scrutinize messages creating urgency like “Act now or lose access!” Such high-pressure tactics are classic giveaways. Be wary of unknown senders, slightly-off email addresses, or unexpected attachments. Scrutinizing grammar, blurry logos, or weird URLs can also reveal deception.
The best lesson? Real-world (but safe!) examples. Show them fake invoices, bank alerts, or “Nigerian prince” emails you’ve received. Point out what looks amiss, reinforcing the golden rule: “when in doubt, don’t click.” This builds their intuitive “spidey sense.”
This principle applies beyond emails to texts (smishing) and calls (vishing). Legitimate organizations will *never* ask for sensitive details like full credit card numbers or passwords via unsolicited communication. Bitdefender’s Scamio can also analyze suspicious links, texts, or QR codes before harm.

9. **Secure Your Smart Devices and Home Network**Our smart homes, filled with IoT gadgets from speakers to cameras, offer convenience but open new cybersecurity risks. These devices can become easy entry points for threat actors into your entire home network if left unsecured. They’re a growing attack surface many families aren’t prepared for.
A major vulnerability lies in weak default settings. Many devices ship with easily guessable credentials like “admin/admin,” rarely changed. Outdated firmware is another issue; IoT devices often don’t prompt for vital security updates, leaving critical loopholes unpatched. Even their control apps can have weak safeguards, exposing private data.
Fortifying your smart home is achievable. First, *immediately* change all default passwords, using strong, unique combinations. Disable any features you don’t need, like remote access, if not regularly used. Fewer open doors mean fewer opportunities for unwanted guests.
Regularly check for firmware updates through the device’s app or manufacturer’s website. These contain critical security patches. For robust defense, segment your network – place smart devices on a separate “guest” or IoT network if your router supports it. This barrier prevents breaches affecting your main computers.
Finally, enable encryption and MFA within device apps wherever available. Think of smart devices as windows into your home: useful, but needing proper closure and securing against unwanted access. Dedicated security software, like NETGEAR Armor, can offer comprehensive protection for all devices.
Read more about: Unlock Warp Speed: 14 Simple Steps to Supercharge Your Internet Connection Today

10. **Create a Family Internet Safety Agreement and Routine**Cybersecurity works best as a shared responsibility, not a solo mission. To cultivate this, consider drafting a simple cyber hygiene plan or agreement as a family. This isn’t about burdensome rules, but establishing common understanding and a culture of safety, ensuring everyone knows their role in protecting the family’s digital well-being.
Your family agreement can define clear expectations for online behavior. This includes specifying acceptable websites and apps, setting device usage hours (perhaps “no-screen” times during meals), and outlining agreed-upon consequences. The goal is a predictable, safe digital environment, like physical safety rules at home, giving everyone clarity and confidence.
Crucially, foster open communication. Create a space where family members comfortably share concerns or suspicions without judgment. A dedicated group chat can be great for flagging potential scams in real-time, allowing everyone to learn and get immediate feedback. Regular reviews of social media and mobile app settings should also be part of this dialogue.
To keep this commitment active, schedule a monthly “Digital Safety Sunday” or similar routine. Collectively check devices, discuss new online trends, and review the agreement. This transforms a chore into a collaborative activity. By revisiting the agreement, your family’s digital safety practices remain relevant and robust.
Read more about: Navigating the Digital Road: A Consumer Reports Guide to Online Car Buying and Selling

11. **Maintain a Judgment-Free Zone for Mistakes**Let’s face it: online mistakes happen. Even tech experts can fall prey to a skilled attacker, whether due to fatigue, distraction, or a convincing scam. When a family member slips up – clicks a bad link, shares too much – the absolute worst reaction is judgment.
If a digital rattlesnake bites, the goal is swift damage control, not an “I told you so” lecture. Eye-rolls or “tsk-tsk” attitudes only make things worse, creating an environment where future incidents go unreported due to embarrassment. This silence is exactly what cybercriminals exploit, giving them more time.
Instead, approach it with empathy and problem-solving. Reassure them it happens to anyone, and the priority is fixing it quickly. Kindness goes a long way, not only in rectifying the current issue but also in fostering trust and encouraging open communication for future challenges.
Of course, rare instances might require locking down accounts or removing privileges after numerous empathetic attempts. However, compassion fosters security far better than condemnation.

12. **Offer Ongoing Support: “I’m Here For You”**Cybersecurity is an ongoing journey, not a finish line. The digital landscape constantly evolves with new threats and technologies. This means teaching good cyber hygiene isn’t a one-and-done conversation, but a long-term commitment. Your role as their digital hero.
Expect more questions, even after covering all habits. Technology surges forward; not everyone keeps pace. Loved ones will encounter new apps, prompts, or scams. Your ongoing presence, willingness to listen, explain, and guide becomes absolutely invaluable.
Don’t hesitate to schedule annual “digital check-ins” or refresher courses. These regular touchpoints allow you to review what’s working, address new concerns, and update them on the latest practices. It reinforces that cyber safety is dynamic and you’re there to help navigate its complexities.
Ultimately, this dedicated approach to digital caregiving builds confidence, independence, and profound peace of mind within your family. Empowered with knowledge and a trusted resource in you, your loved ones will feel safer, making the entire family’s digital footprint stronger and safer.
As we’ve journeyed through these essential cybersecurity habits, it’s clear that safeguarding our families online isn’t about being tech gurus, but embracing informed caution and proactive care. It’s a powerful form of digital caregiving, equipping our loved ones with the resilience to navigate the internet’s complexities with confidence and grace. By patiently fostering healthy suspicion, embracing tools like password managers and MFA, fortifying smart devices, and building a culture of open dialogue and non-judgmental support, we collectively weave a stronger, more secure digital fabric for our families. The online world might be a jungle, but with these habits as our guide, our families can thrive, secure and connected, in its wild beauty.


