
In our increasingly digital lives, where information flows freely and openly, it’s easy to assume everything is right there on the surface. Yet, a fascinating, intricate world of ‘hidden’ digital experiences awaits those curious enough to look a little deeper. From safeguarding your personal photos with clever privacy features on your favorite devices to diving into the captivating puzzles of hidden object games, and even venturing into the often-misunderstood layers of the internet known as the Tor network, there’s so much more than meets the eye. This article is your enthusiastic guide to demystifying these unseen digital realms, offering practical insights and empowering you to explore with confidence and a discerning eye.
Today, we’re not just talking about obscure tech; we’re exploring tools and entertainment that can genuinely enhance your digital life, whether it’s by protecting your most cherished memories or providing hours of engaging gameplay. We’ll break down complex concepts into easily digestible information, making sure you feel informed and ready to make smarter decisions about your online interactions and leisure. Get ready to uncover secrets, master privacy settings, and embark on thrilling digital adventures that promise both utility and excitement.
Our journey begins right on your everyday devices, where ‘hidden’ features offer surprising levels of control over your personal data. We’ll then leap into the delightful world of online gaming, specifically the massively popular genre of hidden object games, before making our way to the more profound depths of the internet: the Tor network. Understanding how to navigate these spaces, what tools are available, and the crucial directories that guide users, is key to truly mastering your digital existence. Let’s peel back the layers and discover the incredible hidden facets of our connected world.
1. Apple’s Hidden Photo Album: Mastering Privacy on Your Devices
For anyone with an iPhone, iPad, Mac, or the cutting-edge Apple Vision Pro, managing your personal photos and videos is a daily task. But what about those moments you want to keep private, away from casual glances or accidental scrolls? Apple has a brilliant, built-in solution: the Hidden album. This feature allows you to control which photos and videos are visible in your main Library, other albums, or even the Photos widget on your Home Screen, moving selected media to a secure, separate location. It’s an incredibly practical and actionable way to maintain your digital privacy with ease.
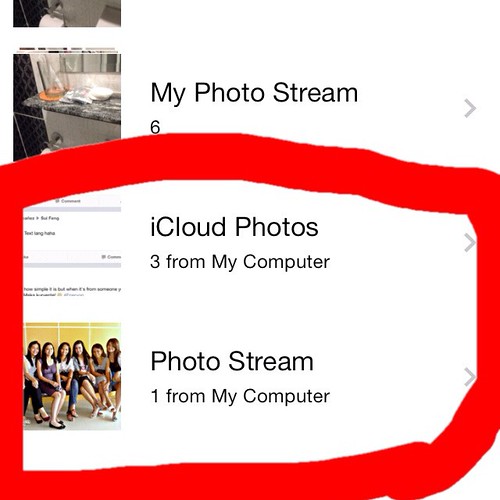
Utilizing the Hidden album on your iPhone or iPad couldn’t be simpler. Just open the Photos app, then tap and hold the photo or video you wish to conceal. A contextual menu will appear, and you’ll simply tap ‘Hide,’ followed by a confirmation to move the item to the Hidden album. What’s even better is that if you use iCloud Photos, any media you hide on one Apple device will automatically be hidden on all your other devices too, ensuring a consistent privacy experience across your entire ecosystem. This seamless integration truly empowers you to keep sensitive content out of sight, wherever you are.
Retrieving or viewing these hidden treasures is also straightforward, though with added security for peace of mind. To unhide photos on an iPhone or iPad, open Photos, tap ‘Collections’ (or the sidebar icon on iPad), scroll down, and tap ‘Hidden’ under Utilities. On iOS 16, iPadOS 16.1, and macOS Ventura and later, your Hidden album is locked by default, requiring Face ID, Touch ID, or your passcode to unlock. Once inside, you can tap and hold the item you want, then select ‘Unhide.’ To further enhance privacy, you can even turn off the visibility of the Hidden album itself in iOS 14 and later, by going to Settings > Apps > Photos and turning off ‘Show Hidden Album.’ This makes the hidden content completely invisible within the Photos app.
Mac users will find a similarly intuitive process. To hide a photo or video, open Photos, then Control-click the item and choose ‘Hide Photo.’ Alternatively, you can use the menu bar by selecting Image > Hide Photo, or simply press Command-L for a quick shortcut. To unhide, navigate to Photos, choose View > Show Hidden Photo Album from the menu bar, then select ‘Hidden’ in the sidebar under Utilities. After authenticating with Touch ID or your login password, you can Control-click the desired photo and select ‘Unhide Photo,’ or use Image > Unhide Photo from the menu bar or press Command-L. Just remember that the Hidden album is off by default on Mac, so you’ll need to turn it on to see it in the sidebar.
For those embracing the immersive experience of Apple Vision Pro, hiding photos is just as simple. In the Photos app, select and hold the photo or video, then tap ‘Hide’ and confirm. Unhiding involves tapping ‘Collections’ in the sidebar, scrolling to ‘Hidden’ in Utilities, tapping ‘View Album,’ and using Optic ID or your passcode to unlock. To unhide a single item, tap and hold its thumbnail and tap ‘Unhide.’ For multiple items, tap ‘Select,’ choose your photos/videos, tap the More button, then ‘Unhide.’ To completely turn off the Hidden album’s visibility, go to Settings > Apps > Photos and toggle ‘Show Hidden Album’ off. These comprehensive tools ensure your most private moments remain truly private across all your Apple devices, giving you ultimate control.

2. The Engaging World of Hidden Object Games: A Casual Gaming Guide
Stepping away from device privacy, let’s dive into a delightful digital pastime: Hidden Object games. These aren’t just games; they’re engaging brain teasers, perfect for sharpening your observation skills and providing a relaxing escape. Whether you’re a seasoned gamer or just looking for a fun way to pass the time, these seek-and-find adventures offer endless object-finding fun without the commitment of complex storylines or steep learning curves. They are truly an accessible and enjoyable form of digital entertainment, empowering players of all ages to immerse themselves instantly.
What makes these games particularly appealing is their incredible accessibility. Platforms like WellGames.com offer a treasure trove of ‘free unlimited Hidden Object games no download.’ This means you can dive straight into a new mystery or an exotic locale without the hassle of installations, registrations, or even time limits. Imagine playing instantly, switching between countless adventures seamlessly – it’s perfect for both quick breaks and long gaming sessions, keeping you hooked for hours. The convenience and sheer variety are truly impressive, making it incredibly easy to start your next adventure.
The genre itself is incredibly diverse, offering something for every taste. You’ll find pure Hidden Object games, ranging from easy finding tasks to story-bound Hidden Object Adventure games with elaborate plots and many characters. Beyond the core seek-and-find mechanics, many titles integrate other popular casual gaming elements. For instance, point-and-click adventure games challenge avid puzzlers to not just find items, but also to apply them in different locations, with titles like ‘Shapik: The Quest’ offering classic cross-device play. This evolution of gameplay ensures that the experience remains fresh and captivating.
Even more creative iterations exist within this vibrant gaming world. If you love interior design, house renovation games like ‘Home Makeover’ let you express your creativity by finding objects to earn money and furnish a virtual house. Or perhaps you dream of a lush garden? ‘Mary Knots Garden Wedding’ allows you to realize those garden design dreams. For those with a detective’s keen eye, games like ‘Time Gap,’ ‘Crime City Detective,’ and ‘Twilight Town’ immerse you in twisted storylines, often featuring additional puzzles like bubble games and Match 3. Then there are ‘find the difference’ games, like ‘Rachel Holmes,’ testing your observation skills with subtle changes between seemingly identical pictures. The possibilities for engaging fun are truly endless.
And let’s not forget the pure puzzle-adventure games that are similar to free escape games online, where the goal is to collect objects and hidden clues to solve puzzles and rescue characters. These often feature vibrant colors and friendly characters, making them particularly fun games for girls. Finally, for those who enjoy a nostalgic challenge, games like ‘Mysteriez!’ and ‘ABC Mysteriez!’ were pioneers in the hidden numbers and letters genre, artfully disguising items among everyday objects. The outstanding feature of these online games was that hidden items didn’t disappear, adding an extra layer of attentiveness needed to avoid penalties. In short, WellGames is positioned as a premier destination to play free unlimited Hidden Object games, offering a rich and varied landscape of casual entertainment.
Read more about: From Pixelated Thrills to Global Phenomenon: The Unstoppable Journey of Sega’s Iconic Speedster, Sonic the Hedgehog
3. Understanding The Hidden Wiki: Your Gateway to the Tor Network
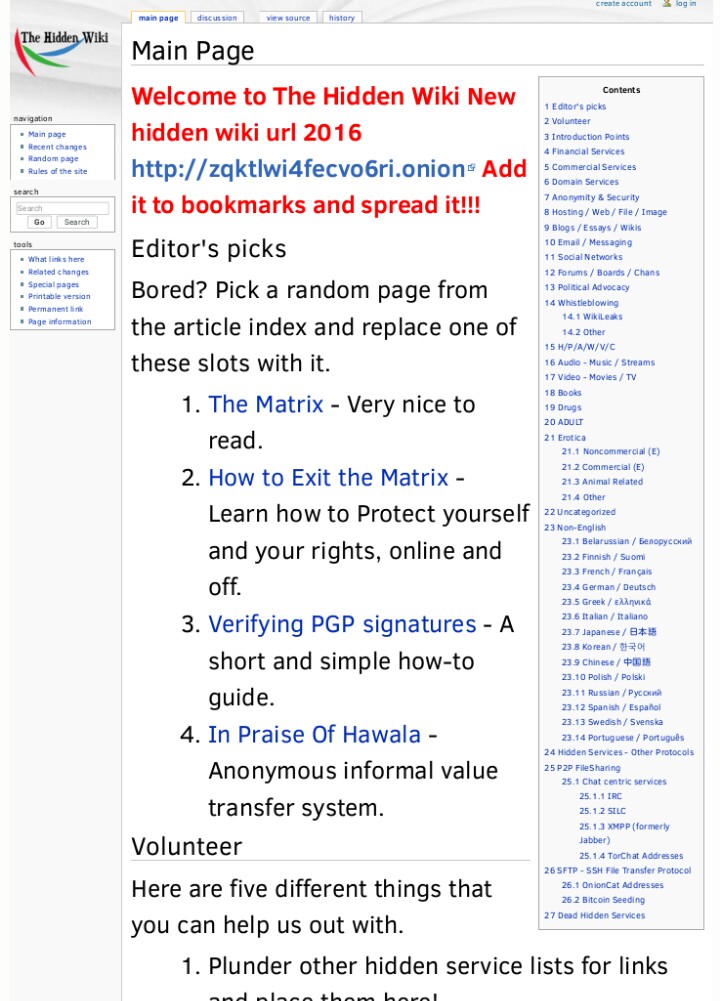
Shifting gears from playful hidden objects to the more serious ‘hidden’ aspects of the internet, we arrive at The Hidden Wiki. This isn’t a game, but a crucial index for anyone looking to navigate the deeper layers of the web, specifically the Tor network. Described as ‘the easiest way to find information on the Tor network,’ The Hidden Wiki serves as a directory of .onion sites, providing a curated list of ‘only working links and trusted sites.’ For anyone interested in exploring beyond the surface web, understanding this platform is your foundational step.
Accessing The Hidden Wiki, and indeed the entire Tor network, requires a specific tool: the Tor browser. This specialized browser, which you can install from http://torproject.org/, is designed to anonymize your internet traffic by routing it through a global network of volunteer-operated relays. Once you have the Tor browser, The Hidden Wiki becomes accessible, acting as a crucial starting point to discover various services and communities operating within this encrypted environment. Think of it as a highly specialized search engine for the hidden corners of the internet, empowering users to discover content that might otherwise be inaccessible or censored.
The importance of The Hidden Wiki extends beyond just providing links. It functions as a community-driven resource, with a dedicated volunteer section highlighting ways people can contribute to its upkeep and accuracy. Volunteers are encouraged to ‘plunder other hidden service lists for links and place them here,’ ‘set external links to HTTPS where available,’ and even ‘start recording onionland’s history.’ This collaborative effort ensures the directory remains robust and up-to-date, making it a reliable resource. Furthermore, tasks like ‘Perform Dead Services Duties’ and ‘Remove CP shitness’ underscore a commitment to maintaining a functional and ethically responsible index, even in the decentralized and often controversial realm of the dark web.
It’s vital to grasp the concept of The Hidden Wiki’s legal standing. The platform itself exists in a ‘complex legal gray area.’ While ‘accessing the Hidden Wiki itself is not explicitly illegal in most jurisdictions,’ the content it links to can certainly be unlawful. This distinction is paramount: the directory is a tool, and its legality for a user largely hinges on how they interact with its references. Cybersecurity experts emphasize that the primary legal concerns ‘stem not from the Hidden Wiki’s existence but from the potential exposure to unlawful content and services it may reference.’ Therefore, navigating The Hidden Wiki, while informative, demands extreme caution and a clear understanding of legal boundaries, ensuring consumer empowerment through knowledge rather than reckless exploration.

4. Essential Tor Network Directories and Search Engines: Navigating the Hidden Internet
Once you’ve grasped the basics of The Hidden Wiki, you’ll discover that it’s just one piece of the puzzle for navigating the Tor network. The hidden internet, or ‘onionland’ as it’s sometimes called, is vast and ever-changing, making reliable directories and search engines absolutely essential. These tools empower users to efficiently find what they’re looking for, whether it’s a specific service, news, or a community, transforming a potentially daunting search into a manageable exploration. Knowing these key resources is like having a well-stocked toolbox for your deep dive.
Among the top introduction points and navigational aids, several stand out for their specific functions and reliability. **GoDark** is highlighted as providing ‘Top Web Sites + Verified,’ aiming to be ‘the easiest and safest way to find the right website.’ This focus on verification is invaluable in an environment where trustworthiness can be a significant concern. For those who prefer to search from the clearnet but for Tor services, **Ahmia.fi** offers a dedicated ‘Clearnet search engine for Tor Hidden Services,’ bridging the gap between the visible and hidden internet.
For general searching while maintaining anonymity on Tor, **DuckDuckGo** offers ‘A Hidden Service that searches the clearnet.’ This allows users to perform standard web searches without leaving the Tor network, combining the privacy of Tor with the utility of a conventional search engine. Community-driven resources are also vital, with the **Tor Link List** providing ‘Community voted links,’ which often serves as a good indicator of popular and useful sites. Conversely, the **Tor Scam List** is a critically important resource for anyone considering transactions on the dark net, acting as ‘one of the most useful list if you want to buy something,’ empowering users to avoid fraudulent services.
Dedicated Tor search engines further enhance navigability. **Torch** is a notable example, boldly claiming ‘to index around 1.1 Million pages,’ demonstrating the scale of searchable content available. Another valuable link collection is **OnionLinks**, which ‘calls itself the Hidden Wiki mirror,’ indicating its comprehensive nature and its role in providing alternative access points to hidden services. Even historical resources play a part, with ‘The Hidden Wiki – The old v2 mirror’ noted as being ‘Here for archive purposes,’ reminding us of the network’s evolution. These tools collectively provide a robust framework for discovering and accessing the diverse offerings of the Tor network.
Finally, for a broader understanding of how to protect yourself online, beyond just finding sites, the **Self-defense Surveillance Guide** offers ‘Tips, Tools and How-tos for Safer Online Communications (clearnet).’ While not strictly a Tor directory, it complements the ethos of privacy and security that draws many to the hidden internet. By leveraging these diverse search engines, link lists, and guides, users can confidently and effectively explore the hidden digital landscape, making informed choices and maximizing their travel through the Tor network with an enthusiastic and empowered approach.
5. Anonymity and Security Tools on Tor: Shielding Your Digital Identity
Venturing into the Tor network is often driven by a fundamental desire for anonymity and enhanced security. While the Tor browser itself provides a significant layer of protection, there are specialized tools and services available within the network that further empower users to shield their digital identity. Understanding and utilizing these resources is crucial for anyone serious about maintaining their privacy and navigating the hidden internet with confidence, turning complex security concepts into practical, actionable steps for consumer empowerment.
One of the most robust additions to your anonymity toolkit is a Virtual Private Network (VPN) designed to work with Tor. **Cryptostorm** is explicitly mentioned as ‘Tor’s own secure VPN service,’ offering a dedicated solution for users. Beyond this, there are generic ‘[1] – VPN provider that supports VPN over Tor.’ The concept here is layering: by routing your VPN traffic through the Tor network, you create a multi-layered shield, making it significantly harder to trace your online activities back to you. This combination provides a powerful defense against surveillance and tracking, embodying practical and actionable advice for maximizing digital security.
For those seeking to maintain extreme pseudonymity or to generate new identities for specific purposes, specialized tools exist. The **Fake ID Generator** provides ‘Fake Identity Name, SSN, Driver’s License, and Credit Card Numbers Generator.’ While the ethical implications of such a tool are significant and demand careful consideration, its existence highlights the lengths to which individuals can go to separate their real-world identity from their online presence. It’s a stark reminder of the unique capabilities available in the hidden parts of the internet, pushing the boundaries of what’s possible in terms of anonymity.
Another essential tool for assessing your current level of anonymity is **BrowsInfo**. This service allows you to ‘Check your anonymity and browser traceability,’ providing valuable feedback on how well your current setup is protecting your digital footprint. It’s a practical way to test your defenses and identify potential vulnerabilities before engaging in sensitive activities. This kind of self-assessment is key to the consumer-empowering philosophy of informed digital interaction, offering concrete data to guide your security choices.
Looking to the future of anonymous online interactions, **Skynet Anonymous Ecology** presents an intriguing development. It’s described as a ‘Blockchain technology based anonymous internet ecology’ designed to ‘Help tor users avoid snooping Tor nodes track location.’ This innovative approach leverages decentralized ledger technology to provide a novel form of protection against common tracking methods on the Tor network. The continuous evolution of such tools demonstrates a vibrant and enthusiastic pursuit of ever-greater anonymity and security, ensuring that users have access to advanced solutions for shielding their digital identity in an increasingly monitored world.

6. Darknet Versions of Popular Clearnet Sites: Familiar Platforms in the Shadows
The Tor network isn’t solely a haven for obscure or illicit activities; it also hosts official, privacy-enhanced versions of many popular clearnet sites. This provides a fascinating bridge between the visible and hidden internet, allowing users to access familiar platforms with the added benefits of Tor’s anonymity and censorship resistance. Discovering these darknet counterparts can be an exciting revelation, offering a different way to interact with services you already know and trust, all while upholding the principles of consumer-empowerment through informed choice.
Many prominent organizations and projects have established an official presence on the Tor network, signaling a commitment to privacy and accessibility for all users, regardless of their location or internet restrictions. For instance, **Tor Project** itself has ‘The official site of the project you’re currently using,’ reinforcing the network’s legitimacy. Major news outlets also embrace this, with ‘The New York Times Secure Drop,’ ‘Deutsche Welle,’ and ‘BBC News’ all offering official .onion sites. These secure drop and news sites are vital for journalists, whistleblowers, and anyone seeking unbiased information without fear of surveillance or censorship.
Communication and file-sharing platforms are also well-represented. **Protonmail** has its ‘Onion version,’ providing an even more secure way to use its privacy-focused email service. For general entertainment, **PornHub** offers ‘The Onion version of the popular porn site,’ and torrent enthusiasts will find ‘The Pirate Bay’ and ‘The Pirate Bay Forum’ available as ‘Onion versions.’ These examples illustrate that the dark web is not just about secrecy but also about offering alternative, more private access routes to a wide array of content and services, catering to diverse user needs.
Even financial transactions and social networking have a hidden presence. **LocalMonero.co** allows users to ‘buy and sell Monero here, via it’s .onion domain,’ providing a privacy-centric option for cryptocurrency exchange. Perhaps most surprisingly, **Facebook** maintains ‘Facebook’s official Onion version,’ claiming ‘not to keep logs.’ While the advice ‘Trust them at your peril’ wisely cautions users, its existence demonstrates how even major social media giants are recognizing the need for Tor access. This accessibility highlights the dark web’s growing integration into our digital landscape, even for seemingly open platforms.
Beyond these, critical infrastructure projects focused on security and anonymity also have their onion sites. **Whonix** and **Qubes OS**, both operating systems highly valued by privacy advocates, offer their official onion presences. Even government entities like the ‘National Police of the Netherlands’ and ‘The CIA’ have ‘Official Onion Sites,’ further emphasizing the dual nature of the dark web as a space for both transparency and covert operations. This remarkable array of official darknet sites demystifies the Tor network, showing it as a powerful tool for secure and private access to a broad spectrum of online resources, turning the perceived ‘shadows’ into a legitimate and often essential part of the internet.” “_words_section1”: “1945

7. Financial Services on the Dark Web: Navigating Decentralized Transactions
The dark web, an often-misunderstood segment of the internet, hosts a range of financial services that operate outside conventional regulatory frameworks. These services cater to users seeking anonymity, bypassing traditional banking systems, or engaging in transactions for various reasons, sometimes legitimate and sometimes less so. Understanding these offerings is key to comprehending the full spectrum of activities taking place on the Tor network, empowering users with knowledge about this unique financial landscape.
Within this hidden realm, you’ll find everything from exchanges for cryptocurrencies to platforms dealing in pre-shredded fiat currency. Services like “Dark Web Wolf Street” explicitly offer to “Buy Pre-Shredded USD & EURO Currency for a fraction of the value,” or even “Buy real money,” showcasing a unique approach to currency acquisition. This highlights a primary characteristic of dark web finance: a focus on bypassing traditional, traceable financial routes, often with significant discounts or unconventional methods that appeal to those prioritizing discretion above all else.
Beyond raw currency, there’s a bustling market for prepaid cards and money transfer services. Platforms such as “Imperial Market,” “Cash Cards,” “Light Money,” and “Millioner Private Club” advertise prepaid Visa, Mastercards, Amex, and money transfers via Western Union and PayPal. These services often promise rapid transfers, sometimes “within 30 minutes,” and focus on ease of access, catering to those who might not have access to traditional banking or prefer to keep their financial activities off-the-books. “Bankor” even claims to offer “Cloned/Prepaid Credit Cards” and transfers, while “Premium Cards” focuses on “Top quality Us & Eu credit cards,” revealing the diverse and often illicit nature of these financial instruments.
These dark web financial services, while offering avenues for anonymity and bypassing conventional systems, come with inherent risks. The lack of regulation means there’s little to no consumer protection, and the potential for fraud is extremely high, as underscored by the existence of resources like the “Tor Scam List” mentioned earlier. Users are expected to proceed with extreme caution, as the allure of discounted currency or anonymous transfers can quickly lead to financial loss or exposure to illegal activities. Navigating these platforms requires a discerning eye and a deep understanding of the risks involved.

8. Commercial Offerings and Marketplaces: Products and Services in the Shadows
Venturing further into the dark web’s commercial landscape reveals an incredibly diverse marketplace, far beyond just financial tools. Here, you can find a surprising array of goods and services, some legal, some in a legal gray area, and many outright illicit. It’s a reflection of human demand, where anonymity allows for the transaction of items that would be difficult or impossible to acquire through conventional channels, providing an alternative economy for those who know where to look.
The offerings range from digital products to physical goods. “Digital Goods” proclaims itself as the “Best Shop for Gift Cards, Payment Cards, Money Transfer and more,” appealing to those seeking immediate digital assets. On the more tangible side, “Apples4Bitcoin” offers “Cheap Apple products for Bitcoin,” a tantalizing prospect for tech enthusiasts willing to navigate the dark web for a deal. Conversely, “EuroGuns” boldly positions itself as “Your #1 European arms dealer,” clearly stepping into a highly illegal and dangerous territory, showcasing the stark contrast in the types of goods available.
Services are also a significant part of this hidden economy. “Rent-A-Hacker” presents the opportunity to “Hire a hacker for every job you can imagine,” a service that immediately raises ethical and legal questions but points to a demand for specialized, often covert, digital skills. For those needing to verify identity, “Onion Identity Services” offers “Selling Passports and ID-Cards for Bitcoins,” a service with obvious illicit uses. And to facilitate these transactions, “Dark Escrow” provides an “Escrow service for your dark net transactions,” a crucial mechanism for building trust in an environment inherently lacking it, highlighting a practical solution to a pervasive dark web problem.
The existence of such marketplaces underscores the dual nature of the dark web: a place for privacy, but also a breeding ground for illicit commerce. While consumer empowerment often means having more choices, in this context, it also comes with the weighty responsibility of understanding the legal and ethical ramifications. The sheer variety of “Commercial Services” listed, from “Kamagra for Bitcoin” (a cheaper alternative to Viagra) to “Storex Samsung All kinds of products with escrow,” paints a vivid picture of a bustling, albeit hidden, global marketplace operating under a different set of rules.
9. Anonymous Communication Platforms: Email, Messaging, and Social Networks
One of the most compelling reasons users flock to the Tor network is the promise of truly anonymous and secure communication, allowing for free expression and information exchange without fear of surveillance or censorship. The dark web hosts a vibrant ecosystem of platforms designed specifically for this purpose, offering everything from encrypted email to private messaging and even social networking, all built with privacy at their core. These tools empower individuals to connect and share in ways that might be restricted or monitored on the clearnet.
Email services form a critical part of this anonymous communication infrastructure. “Mail2Tor” stands out as a “free anonymous e-mail service made to protect your privacy,” offering a crucial layer of secrecy for correspondence. Similarly, “TorBox” is a “hidden mailbox service only accessible from TOR without connection with public internet,” ensuring that communications remain entirely within the encrypted network. Even established clearnet privacy providers like “Protonmail” offer an “Onion version,” leveraging Tor’s anonymity alongside their end-to-end encryption for maximum security. These services cater to a fundamental need for private digital communication.
Beyond email, instant messaging and chat platforms thrive on the dark web, providing real-time, encrypted interactions. “Chator” offers “Tor based PGP encrypted chat with multiple anonymous aliases per account,” giving users a robust tool for secure conversations. “KeyBase” is highlighted as a platform for “secure messaging and file-sharing,” demonstrating the integration of multiple privacy features. For a more decentralized approach, “GoTor Messenger” is an “Open-source Peer-to-peer-encrypted messenger with semi-federated network,” emphasizing community control and enhanced privacy protocols. These diverse platforms ensure that users have choices for truly private discussions.
Perhaps most surprisingly, even social networking has found a home on the dark web. “Galaxy3” proudly declares itself “a new, Social Networking experience for the darknet!” offering a space for anonymous interaction and community building. Most notably, “Facebook” maintains its “official Onion version,” claiming “not to keep logs,” though the context wisely adds the caveat “Trust them at your peril.” This inclusion of major platforms on the dark web highlights a growing recognition of the demand for privacy-focused access to common services, even if users must remain vigilant about the true extent of their anonymity on such large platforms.

10. Whistleblowing and Investigative Journalism: Unveiling Truths Anonymously
In an era where transparency and accountability are paramount, the dark web has emerged as a crucial conduit for whistleblowers and investigative journalists to share sensitive information without fear of reprisal. This hidden corner of the internet provides a secure and anonymous channel for individuals to expose wrongdoing, report on injustices, and contribute to public interest journalism, acting as a vital mechanism for upholding democratic values and empowering citizens with critical information. The existence of these platforms underscores the dark web’s potential for profoundly positive societal impact.
At the forefront of this movement is “SecureDrop,” an “open-source whistleblower submission system managed by Freedom of the Press Foundation.” This platform allows sources to anonymously submit documents and tips to news organizations, ensuring their identities are protected. Similarly, major news outlets like “The New York Times Secure Drop” and “The Guardian” operate their own official onion sites for whistleblowing, demonstrating a commitment to protecting sources and facilitating the flow of vital information that might otherwise be suppressed. These dedicated channels are invaluable for fearless, adversarial journalism that holds the powerful accountable.
Beyond direct submission platforms, the dark web also hosts organizations dedicated to investigative journalism and information dissemination. “ProPublica,” known for its “Investigative Journalism and News in the Public Interest,” maintains an official presence, ensuring its critical reporting reaches audiences even in censored regions. “AfriLeaks” offers a specialized platform for blowing the whistle, highlighting the global reach and necessity of these anonymous reporting tools. These sites are not merely repositories but active participants in the pursuit of truth, leveraging the dark web’s anonymity features for public good.
The importance of these whistleblowing platforms cannot be overstated, especially when juxtaposed with entities like the “National Police of the Netherlands” and “The CIA” also having official onion sites, indicating the complex interplay of information gathering and dissemination in the digital age. They empower individuals to speak truth to power, offering a vital counter-narrative to official channels and enabling a more informed citizenry. However, users must always remember to follow secure practices, even when engaging with seemingly legitimate whistleblowing sites, as the environment demands constant vigilance to maintain anonymity.

11. The Digital Underbelly: Hacking, Hosting, and File Sharing Services
Beneath the surface of anonymous communication and whistleblowing, the dark web also hosts a specialized array of services that delve into the more technical, and sometimes controversial, aspects of the internet: hacking communities, decentralized hosting solutions, and secure file-sharing utilities. These platforms cater to a diverse user base, from privacy-conscious developers to individuals exploring the fringes of cybersecurity and digital autonomy, offering tools and resources that empower a different kind of digital interaction.
Hacking, phreaking, and anarchy-related communities find a space here, often driven by ideologies of digital freedom and information liberation. “RiseUp” provides “online communication tools for people and groups working on liberatory social change,” acting as a hub for activists and technologists. Forums like “HeLL Forum” (HeLL Reloaded is back!) cater to discussions around hacking, while “DefCon” serves as the “Home of Hacking conferences,” albeit in a hidden digital form. These communities often share knowledge, tools, and discussions on cybersecurity, sometimes blurring lines between ethical exploration and potential misuse, underscores the need for awareness when engaging with such content.
For those seeking to establish a presence within the Tor network itself, anonymous hosting services are crucial. Providers like “Kaizushi’s Little Onion Server” and “SporeStack” offer “Darknet hosting on a secure Gentoo Hardened platform” or “API-driven VPS hosting for Bitcoin,” providing infrastructure for websites that prioritize anonymity. “Daniel’s Hosting” offers “Free hosting solution only for a non-commercial personal project,” demonstrating a commitment to supporting independent and privacy-focused content creators. These services empower users to build and maintain an anonymous online presence, fostering a more decentralized internet.
Finally, secure and anonymous file uploaders are essential for sharing documents and media without leaving a traceable footprint. Beyond “SecureDrop” for whistleblowing, platforms like “BlackCloud,” “Keybase,” and “Megator” offer “minimalist, but useful .onion pastebin” or “good pastebin with end-to-end encryption,” and robust file uploading capabilities. These tools, alongside “Etherpad” for collaborative text editing and “ZeroBin” for server-knowledge-free data pasting, ensure that sensitive information can be shared and collaborated upon securely within the Tor network, providing practical solutions for those needing discreet digital exchanges.
12. The Complex Legal Landscape of the Dark Web: Navigating the Boundaries
Venturing into the dark web is an exercise in navigating a complex and often ambiguous legal landscape. While the Tor network itself and basic access to sites like The Hidden Wiki are generally not illegal, the vast majority of activities and content found within its deeper layers can carry significant legal consequences. Understanding these boundaries is absolutely paramount for any user, transforming potential risks into informed decisions and embodying the core principle of consumer empowerment through knowledge.
The legal status of platforms like The Hidden Wiki exists in a “complex legal gray area.” As the context states, “While accessing the Hidden Wiki itself is not explicitly illegal in most jurisdictions, many of the sites it links to may contain illegal content or facilitate unlawful activities.” This crucial distinction means that merely opening the Tor browser and visiting a directory is usually permissible, but the responsibility shifts entirely to the user once they begin exploring the linked content. Cybersecurity experts emphasize that primary legal concerns “stem not from the Hidden Wiki’s existence but from the potential exposure to unlawful content and services it may reference.”
Users must recognize that “the repercussions of accessing illegal content through dark web sites can be severe.” Law enforcement agencies worldwide actively “monitor suspicious activities,” and individuals caught engaging with prohibited goods, services, or information “may face criminal charges.” This is a stark reminder that the anonymity offered by Tor is not absolute, and authorities are increasingly sophisticated in their ability to track and prosecute illicit activities. The decentralized and encrypted nature of the dark web makes regulation challenging, but it does not equate to immunity from legal accountability.
Therefore, “user responsibility plays a crucial role in determining legal compliance.” Steps to safely navigate the dark web include using a reputable VPN, verifying site authenticity, keeping the Tor browser updated, never sharing personal information, and monitoring system resources for suspicious activity. Even with these precautions, the “Risks Of Using The Hidden Wiki For Unsanctioned Activities” remain high, including “Exposure to malware and ransomware attacks,” “Potential identity theft and data breaches,” and “Scams and fraudulent services.” Empowering users means equipping them with both the tools and the critical understanding of these inherent dangers, fostering a cautious and informed approach to dark web exploration.
Read more about: Miss the ’90s? These 14 Earth-Shaking Events Defined a Decade of Unprecedented Change—Their Impact Still Resonates!
As we conclude our deep dive into the hidden facets of the digital world, from device privacy features and engaging hidden object games to the intricate layers of the Tor network and the diverse offerings of the dark web, one truth becomes abundantly clear: knowledge is power. The digital landscape, with its visible and hidden components, offers incredible tools for privacy, information access, and entertainment. By understanding how to navigate these spaces, recognizing the potential, and exercising informed caution, you are truly empowered to make smarter decisions, protect your digital identity, and explore the unseen with confidence. This journey has hopefully equipped you with the insights needed to become a more discerning and adventurous digital citizen, ready to uncover the next hidden secret that awaits.



