
In an increasingly connected world, the threat of identity theft looms larger than ever. It’s a tricky beast, isn’t it? Unlike a prized heirloom you can lock away, your personal information is out there, constantly used for everything from taxes to job applications, making it seem impossible to protect. But here’s the empowering truth: while identity theft is on the rise – with over 1.1 million cases reported in 2024, and more than $10 billion in losses in 2023 – you are far from helpless.
The sheer volume of fraud reports, where identity theft leads as the top complaint, can feel overwhelming. Scammers are relentless, leveraging everything from data breaches to sophisticated AI-powered attacks like voice cloning and AI-generated content to exploit vulnerabilities across all generations. But don’t despair! Just as there are countless ways for thieves to steal your data, there are just as many, if not more, practical and easy-to-manage practices you can adopt to safeguard your personal information and stop identity thieves in their tracks. It’s about being smart, proactive, and making some crucial lifestyle adjustments, both online and off.
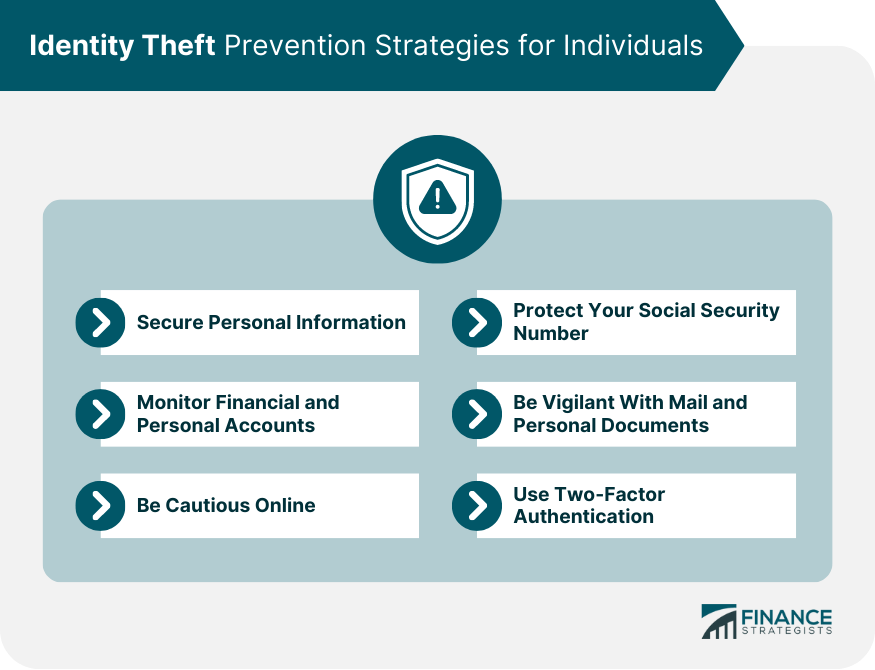
This in-depth guide is designed to empower you with a comprehensive defense plan. We’ve compiled 14 essential strategies, straight from the experts, to help you navigate this complex landscape. From fortifying your digital accounts to securing your physical mail, these actionable steps will help you build a multi-layered shield around your identity. Let’s dive in and transform uncertainty into unwavering security, equipping you with the knowledge and tools to protect yourself and your loved ones from this pervasive threat.

1. **Invest in an Identity Theft Protection Service**It might seem like an obvious first step, but the value of an identity theft protection service cannot be overstated. We all try our best to keep an eye on our finances and credit reports, but these services offer a level of vigilance and advanced features that are simply not reasonably available to individuals on their own. Think of it as having an always-on guardian for your most sensitive data.
These services go beyond basic monitoring. They can provide real-time notifications if your personal data is used to open a new account, or alert you if your information appears on the dark web, where stolen credentials are often traded. This early warning system is incredibly powerful, allowing you to react quickly before a small breach escalates into a major crisis. It’s about being informed the moment something suspicious happens, not weeks or months later.
While this strategy might require a bit more of an investment compared to some other free tips, its comprehensive nature makes it invaluable. The peace of mind and the enhanced protective features it offers can far outweigh the cost when you consider the potential long-term consequences and financial losses associated with identity theft. Consider it a foundational layer in your overall identity defense plan.
Read more about: Spotting the Hidden Traps: A Comprehensive Guide to Protecting Older Adults from Sophisticated Financial Scams

2. **Collect Mail Daily & Manage Physical Documents**Your mailbox, seemingly innocuous, can be a treasure trove for identity thieves. Documents containing personally identifiable information (PII) like credit card statements, utility bills, healthcare forms, and even pre-approved credit card offers are all potential targets. Thieves can intercept this mail, gleaning enough information to impersonate you or open new accounts in your name.
Making a habit of collecting your mail every single day is a simple yet effective deterrent. This routine minimizes the window of opportunity for opportunistic thieves. Furthermore, if you plan to be away from home for more than 24 hours, it’s wise to place a mail hold with USPS. This ensures your mail isn’t left piling up, signaling an empty home and an easy target.
Beyond collection, the proper disposal of sensitive documents is paramount. Remember those document shredders that used to be everywhere? They still serve a vital purpose! Identity thieves are not above digging through trash for documents containing PII. Even seemingly harmless items like boarding passes can provide enough initial information for a talented thief. If a document has personal information on it – shred it. Consider investing in a cross-cut or micro-cut shredder for maximum security, or look for community shredding events. Opting for paperless billing whenever possible can also significantly reduce your paper trail and your risk.
Read more about: Review: The New iPhone Feature That Could Replace Your Wallet – iOS 26’s Wallet Overhaul Examined

3. **Regularly Review Credit Card and Bank Statements**One of the most common ways financial identity theft is caught is through diligent review of credit card and bank statements. In fact, credit card fraud stands as the most frequent type of identity theft. Scammers often start with small, seemingly insignificant transactions to test the waters and see what they can get away with before attempting larger fraudulent activities.
This means you need to be meticulous. Carefully scrutinize every transaction listed on your statements. Look for any charges that seem unfamiliar, whether it’s a merchant you don’t recognize, an unexpected location for a purchase, or even a transaction for an amount that doesn’t quite match your memory. Even small discrepancies could be the first sign of a larger problem.
Should you spot anything suspicious, don’t hesitate. Immediately contact your credit card company or bank to dispute the charges and request a new card. Many banking platforms and financial institutions also offer options to sign up for alerts – receiving a text every time you make a purchase might seem annoying, but these real-time notifications can be a lifesaver, sparing you the headache of dealing with fraudulent transactions long after they’ve occurred.
Read more about: Aron Bell, Last Brother of a World War II Resistance Group, Dies at 98: A Legacy of Courage and Rescue

4. **Freeze Your Credit Reports**When it comes to building an impenetrable shield against identity theft, freezing your credit is one of the most powerful and effective strategies at your disposal. This action restricts access to your credit report, including inquiries, for virtually everyone – even yourself, unless you temporarily lift the freeze. Since most businesses and credit lenders require checking your credit history before approving new accounts, a credit freeze effectively prevents thieves from opening new lines of credit in your name.
The beauty of a credit freeze is its simplicity and reversibility. It’s completely free to implement and will not negatively impact your credit score. To put a freeze in place, you’ll need to contact each of the three major credit reporting agencies: TransUnion, Equifax, and Experian. They provide mail-in request addresses or online portals for this process, making it quite accessible.
This measure is especially recommended for children in your household. Children are just as vulnerable to identity thieves, and malicious activity on their credit can go unnoticed for years, often until they apply for their first credit card or student loan. This extended period between the crime and its discovery can make it much harder to remedy. A credit freeze, coupled with a close eye on their credit reports, can stop these issues before they even begin, giving them a clean financial slate as they grow.
Read more about: Unlock Significant Savings: 12 Expert Strategies to Effectively Lower Your Property Taxes Before Year-End

5. **Create Strong, Unique Passwords & Use a Password Manager**We all know the temptation to use easy-to-remember passwords or, worse, the same password across multiple accounts. But let’s be blunt: this is a catastrophic security gamble. If an identity thief manages to compromise one account where you’ve reused a password, they will immediately attempt to use those same credentials on every other account they can think of, from your banking to your social media. This exponentially increases your risk.
The FBI and the National Institute of Standards and Technology recommend passwords with at least eight characters, as they are significantly harder for computers to crack. But beyond length, aim for complexity: a mix of upper and lowercase letters, numbers, and symbols. And for goodness sake, avoid predictable sequences like ‘12345678’ or the word ‘password’ itself! Variety is your best friend here; avoid using very similar passwords across different platforms.
Managing a multitude of complex, unique passwords might seem daunting, but that’s where password managers shine. These services or apps create strong, unique passwords for you and then store them securely in encrypted digital vaults, accessible only to you. This means you only need to remember one master password for the manager, and it handles the rest. This trick saved our Privacy and Technology editor when their identity was compromised after a data breach; because they used different passwords for different accounts, hackers were locked out of their bank accounts, and they were promptly notified of the failed login attempts.
Read more about: The Essential Guide to Building an Unbreakable Home Wi-Fi Network: 14 Steps to Digital Peace of Mind
6. **Enable Two-Factor Authentication (2FA) on Devices and Accounts**Adding two-factor authentication (2FA) to your devices and online accounts might feel like an extra step, an annoying delay in your digital life. But those few extra seconds of verification are not just a convenience; they are a critical security barrier that can be a genuine lifesaver. This system requires two distinct forms of verification – typically your username and password, plus a second factor like a one-time code sent to your phone via SMS, an authentication app code, or a biometric scan.
The power of 2FA lies in its ability to protect your accounts even if a scammer somehow gets their hands on your passwords. Without that second factor, your password alone is useless to them. It’s like having two locks on your front door; even if a thief picks the first lock, they still can’t get in. This makes your accounts several times harder to hack, significantly reducing the chances of a successful breach.
We strongly recommend enabling 2FA on every account that offers it. Prioritize your email accounts, as these are often the keys to resetting passwords for other services. Then, extend this protection to your social media profiles, banking and credit card accounts, and any other website that stores personal data about you. This seemingly small action creates a formidable defense layer, ensuring that even if your password is compromised, your sensitive information remains secure.
Read more about: The Smartest Ways to Protect Your Online Privacy in 2025: An Essential Lifehacker’s Guide
7. **Install Antivirus or Other Protection Software**In the digital realm, your devices are constantly exposed to invisible threats – viruses, malware, and spyware. These insidious programs are cybercriminals’ tools of choice for stealing personal information, monitoring your online activity, and generally wreaking havoc. Fortunately, robust protection software acts as your digital immune system, defending against these pervasive dangers.
Antivirus software is designed to protect your devices against viruses and malware, which are essentially ‘bugs’ that can slow down, crash, or compromise your system. It actively scans your emails and files for incoming threats, preventing them from infecting your device before they can cause harm. Think of it as a vigilant guard dog, sniffing out danger before it can enter your home.
Complementing antivirus, antispyware software specifically targets malicious programs that monitor your online activity and collect your personal information without your consent. Furthermore, installing a firewall on your device adds another layer of defense, helping to block incoming threats like hackers and various types of malware from gaining unauthorized access. Expect to pay about $25 to $75 annually for most antivirus software, a small price for significant peace of mind and protection against digital intrusion.
Now that we’ve covered the essential foundational steps, it’s time to elevate your defense game. Identity theft isn’t a static threat; it evolves with technology, meaning your protection strategies must too. This second section focuses on advanced digital hygiene and continuous vigilance, empowering you with the tools to navigate online threats and maintain ongoing security. We’ll explore strategies that mitigate risks from unsolicited offers, maintain credit health, secure old electronics, navigate public Wi-Fi safely, recognize phishing attempts, keep software updated, and manage your social media presence. Each step is designed to build a more robust, adaptable shield around your digital life. Let’s dive into these crucial, proactive measures that empower you to stay several steps ahead of identity thieves.
Read more about: Fortify Your Remote Fortress: 12 Essential Cybersecurity Strategies for US Remote Workers

8. **Opt-out of Prescreened Credit Card Offers**That pile of unsolicited credit card offers and promotional mail isn’t just annoying; it’s a goldmine for identity thieves. These documents contain enough of your personally identifiable information (PII) to be intercepted and misused. A thief could easily snag one of these offers, using your details to open accounts in your name, which they then control. It’s a surprisingly common and low-tech method for fraudsters to get started.
Even if you diligently shred these offers before tossing them, the risk remains. The mere presence of these documents in your mailbox creates an unnecessary vulnerability. Why leave anything to chance when there’s a straightforward way to shut down this particular avenue for identity theft?
The good news is you can cut this threat off at the source. The Federal Trade Commission (FTC) provides a simple process to opt out of receiving these prescreened offers. This action significantly reduces the amount of PII floating around in your physical mail, drastically decreasing the chances of a thief intercepting it.
You have two options for opting out: for a period of five years or permanently. Either way, the process is easy. Simply visit optoutprescreen.com and fill out a request, or call 1-888-5-OPT-OUT (1-888-567-8688) to be guided through the process by an agent from one of the major credit bureaus. It’s a small step that yields significant peace of mind.

9. **Review Credit Reports Annually**Think of your credit report as a detailed financial diary, chronicling every major financial event in your life. By law, everyone is entitled to a free credit report from each of the three major credit bureaus—Experian, Equifax, and TransUnion—annually. This is an invaluable resource you should absolutely leverage, as accessing these reports won’t negatively impact your credit score.
When you download your reports, don’t just skim them. It’s crucial to meticulously examine every detail. Look for any changes to your personal information, such as addresses, account details, or inquiries you don’t recognize. Pay particular attention to any new credit accounts that may have been opened; ensure they align perfectly with requests you’ve personally made during the year.
Furthermore, scrutinize your payment history. If your payment history score seems unusually low, even though you generally pay your bills on time, this could be a red flag. It might indicate that a line of credit has been opened in your name without your knowledge and is not being paid, severely damaging your financial standing.
Should you uncover anything suspicious, first cross-reference it with your personal records to rule out any genuine mistakes. If an entry truly remains unrecognized, don’t delay. It’s imperative to dispute the error immediately with the credit bureau and report the potential identity theft. Leveraging the online portals provided by these agencies makes the process relatively straightforward, helping you swiftly reclaim control of your financial narrative. Remember, consistent vigilance pays off.
Read more about: An In-Depth Profile: Unpacking the Complex Journey of T.O.P (Choi Seung-Hyun)

10. **Wipe Electronics Before Donating/Selling**When it’s time to upgrade your tech, your old electronics—be it a smartphone, tablet, or laptop—often find a second life through donation, sale, or recycling. However, a critical step that many overlook, and one that identity thieves bank on, is thoroughly wiping all personal data from these devices. Failing to do so is like handing over your digital diary to a stranger.
Many assume that simply deleting files sends them into the digital ether, never to be seen again. This, unfortunately, is a dangerous misconception. Even after deletion, remnants of those files often remain on the device. Sophisticated data recovery programs can reassemble these fragments, making your sensitive information—from old photos to financial documents—accessible until it’s properly overwritten.
To truly safeguard your privacy, a simple factory reset isn’t always enough. You need to ensure the data is irrecoverably erased. One highly effective method is using specialized overwrite software designed to wipe hardware completely, essentially writing new, meaningless data over your old files multiple times. This makes data recovery virtually impossible.
Before you let go of any device, make it a non-negotiable rule to remove any physical storage, such as SIM cards from phones or SD cards from cameras and tablets. Once those are removed, perform a factory reset. For computers, consider professional data wiping services or use reputable software that explicitly states it overwrites data. This diligent approach ensures your digital past stays private, even after your devices move on.

11. **Be Cautious Using Public Wi-Fi**That free public Wi-Fi at your favorite coffee shop or airport might seem like a convenience, but it often comes with hidden security risks. Open networks, while easy to access, are a prime hunting ground for cybercriminals. They make it surprisingly simple for scammers to connect to your devices and intercept your data, turning your casual browsing into a potential identity theft hazard.
These unsecured public connections can allow malicious actors to monitor your online activity and steal personal information directly from your phone, laptop, or tablet. Imagine a thief peering over your shoulder as you type in sensitive details; that’s essentially what can happen on an unprotected public Wi-Fi network. They can glean everything from login credentials to financial details without you ever knowing.
The golden rule here is simple: never access your financial accounts, conduct online banking, or make purchases that require sensitive personal information over unsecured public Wi-Fi connections. If it’s something you wouldn’t shout across a crowded room, don’t type it over an open network. Your sensitive data deserves a secure, private connection.
For those times when you absolutely must use public Wi-Fi, arm yourself with a Virtual Private Network (VPN). A VPN encrypts your internet traffic, creating a secure tunnel for your data. This means that even if a hacker manages to intercept your connection, all they’ll see is garbled, unreadable information. It’s an essential layer of protection that ensures your online activities remain private and secure, no matter where you connect.
Read more about: The 12 Unsung Heroes: ‘Dumb’ Tech Gadgets That Actually Deliver Value and Are Worth Every Penny

12. **Don’t Fall for Phishing Scams**Phishing scams are among the most persistent and deceptive threats to your identity. These insidious attacks come in various forms, often disguised as legitimate communications from banks, government agencies, or well-known companies. Scammers use fraudulent emails, texts, or phone calls to trick you into divulging personal or financial information, which they then exploit for their own gain.
The core principle of defense against phishing is unwavering skepticism. As a steadfast rule of thumb, never input personal or financial information simply because an email, text, or website prompts you to. Legitimate organizations rarely, if ever, request sensitive data through unsolicited digital communications. Always assume the worst until proven otherwise.
Before clicking any links or providing information, verify the legitimacy of the sender and the website. Check that the URL precisely matches the official website of the company or entity that supposedly contacted you. Phishing scammers are masters of mimicry; they often create highly convincing fake websites with URLs that are only subtly different from the real ones. A single misplaced letter or an extra dash can be the giveaway.
Beyond URL vigilance, keep an eagle eye out for any grammatical errors, spelling mistakes, or unusual phrasing on websites or in messages. These are often tell-tale signs of a fraudulent attempt. When in doubt, navigate directly to the official website by typing the address yourself or contact the organization through a verified phone number, rather than using any contact information provided in the suspicious communication. Your caution is your best shield.
Read more about: Spotting the Hidden Traps: A Comprehensive Guide to Protecting Older Adults from Sophisticated Financial Scams

13. **Update Your Device Software**It might seem like a minor annoyance when your phone or computer constantly prompts you to install software updates. However, these updates are far more than just feature enhancements or aesthetic tweaks; they are critical security patches designed to protect you from the latest threats. Outdated software versions are often rife with vulnerabilities that hackers actively seek to exploit, leaving your devices and personal data exposed.
Think of software updates as immunization shots for your digital devices. Each new version frequently contains vital security and bug fixes that close loopholes and strengthen your device’s defenses against malware, viruses, and other cyberattacks. Neglecting these updates is akin to leaving your front door unlocked, inviting trouble.
Making a habit of updating your device whenever a new version becomes available is a simple yet profoundly effective security measure. It ensures that your operating systems, applications, and security software are all running with the most current protections, making it significantly harder for cybercriminals to penetrate your digital perimeter.
To make this process seamless and ensure you’re always protected, consider enabling auto-update features on your devices and applications. This way, essential security patches are installed as soon as they’re released, without you having to actively remember to do it. It’s a ‘set it and forget it’ approach to maintaining a strong, up-to-date defense against evolving digital threats, letting your technology work smarter for your safety.
Read more about: The Essential Guide to Building an Unbreakable Home Wi-Fi Network: 14 Steps to Digital Peace of Mind

14. **Be Wary of Social Media**Social media platforms, while fantastic for connecting with friends and family, can also be a significant liability for your identity security if not managed carefully. Prolific social media users often post vast amounts of identifying information online, turning their profiles into rich data sources for resourceful fraudsters. This public sharing can make you an easy target for those looking to piece together personal details.
It’s crucial to enable the strongest security and privacy measures available on all your social media accounts. Platforms like Facebook offer extensive tools to help you assess and protect your account settings. Go beyond the default settings and proactively limit who can see your posts, photos, and personal information. Every piece of public data is a potential clue for a thief.
Be acutely cautious about the information you make public. This includes seemingly innocuous details like your full name, city of residence, employer, and especially your birth date. These pieces of data, when combined with other publicly available information, can be enough for a scammer to impersonate you, reset passwords, or even open new accounts in your name.
Identity thieves are adept at scouring social media accounts for identifying information in posts, photos, and even seemingly innocent online quizzes or surveys that ask for personal details. Regularly review your privacy settings, think twice before sharing sensitive life updates, and be selective with your online interactions. Your vigilance in managing your digital footprint on social media is a powerful line of defense against identity theft.
Read more about: Your Ultimate Guide to Unlocking Massive Savings: The Best Online Deal Sites and Shopping Tools
In a world where digital threats constantly evolve, safeguarding your identity demands ongoing vigilance and proactive measures. By implementing these 14 strategies, from fortifying your digital accounts with advanced authentication to carefully managing your online presence and physical documents, you’re building a comprehensive, multi-layered defense. Remember, the power to protect your personal information lies squarely in your hands. Stay informed, stay cautious, and make these practices a routine part of your life to keep identity thieves stopped dead in their tracks.



:max_bytes(150000):strip_icc():focal(711x326:713x328)/joanna-carson-johnny-carson-080425-ef84ab9a5fe74660a30098f00c611f2b.jpg)