We all value our privacy, but are you really doing everything you can to protect it online? In an age where so much of our lives are intertwined with the digital world, nothing is truly off-limits to those with malicious intent. Technology changes the way people go through their daily lives, transforming the world around them by making sharing documents and files simpler and allowing for quick communication. Smart gadgets and phones make life easier, but they can unfortunately lead to potential security risks if not handled with care.
Hackers are incredibly adept at what they do, constantly seeking vulnerabilities to exploit. With more people than ever working from home, technology is being used in ways it wasn’t before, making vigilance paramount. While technology growth offers many benefits, it can be detrimental if you make privacy mistakes. Knowing the common missteps can help you take the proper precautions and safeguard your digital privacy, ensuring your online experience remains secure and personal.
I’ve spent countless hours testing privacy tools, reading terms of service, and learning from my own mistakes, and I’ve found that most people are still making some critical errors. Hackers target people who make common privacy mistakes because those individuals often don’t know any better. The more devices you use and the more information you put out there, the more entry points you inadvertently offer to cyberspace criminals. Let’s dive in and see if you’re guilty of any of these common privacy no-no’s.
1. **Underestimating Online Risks**If you don’t fully grasp the potential risks associated with using technology online, it’s incredibly difficult to know what dangers to watch out for. Many people, unknowingly, might freely share personal information without a second thought about the consequences. Each time you input your data online, whether it’s for a simple signup or a complex transaction, you become more susceptible to potential hacking attempts and data breaches.
It’s crucial to understand how surprisingly easy it can be for attackers to steal data or introduce harmful malware into your system. This isn’t just about direct attacks; even seemingly innocuous actions like downloading files or apps from unverified sources can introduce significant security issues. Without a clear understanding of these threats, the critical proactive steps needed for protection often go unaddressed.
Your best course of action is to always err on the side of caution and actively avoid giving out personal information through the internet unless absolutely necessary and through verified, secure channels. By adopting a mindset of informed skepticism regarding online interactions, you can significantly reduce your exposure. Recognizing that every piece of information shared online has implications is the first step toward building a robust digital privacy strategy.
Read more about: Mastering the ‘Side’ Game: 12 Zero-Investment Concepts for Unleashing Your Potential

2. **Using Weak Passwords & Poor Storage**Weak passwords represent one of the most glaring and common privacy mistakes, leaving countless individuals vulnerable to being hacked. It’s an open invitation for malicious actors to access your accounts. Using strong, complex, and unique passwords is not just a recommendation; it’s an essential defense for protecting yourself and all your digital devices and data.
Hackers are remarkably skilled at deducing personal information to crack passwords. They frequently browse social media pages, piecing together details about what and who is important to you – birthdays, pet names, significant dates – all of which can be used to guess your passwords and gain unauthorized entry into your accounts. They can quickly identify simple sequences and common patterns, so it’s imperative to avoid using predictable combinations.
Beyond just creating strong passwords, protecting them and storing them reliably is equally vital. Many people don’t protect their passwords adequately and often resort to writing them down in insecure places. A sticky note on your desk, for instance, is one of the least secure options, as anyone passing by can easily obtain that critical information. Even emailing passwords to yourself isn’t always secure, making it a practice best avoided whenever possible. Moreover, many users keep passwords open on their devices, sometimes in plain text, which is an enormous risk.
A robust solution is to use a password manager. Tools like bitwarden can generate strong, unique passwords for every account you have and store them securely, requiring you to remember only one master password. It’s a game-changer for enhancing security and convenience. For maximum security, enable two-factor authentication (2FA) on your password manager and any other critical accounts like email or banking, adding an extra layer of protection even if a password is somehow compromised. Avoid saving passwords directly in your browser, as built-in managers are often less secure, with saved passwords potentially visible in plain text to anyone with access to your computer.
Read more about: Decoding the Digital Underworld: 14 Essential Gadgets for Cyber Security Professionals
3. **Ignoring Software & App Updates**You might be surprised to learn how easily outdated software can become a gateway for hackers. Without regular system updates for your operating system and applications, your devices remain vulnerable and surprisingly easy for cybercriminals to access. These updates aren’t just about new features; they frequently contain critical security patches that fix loopholes and vulnerabilities hackers could otherwise exploit.
Ignoring those persistent “Update Available” notifications might seem like a time-saver, but it’s a significant privacy mistake. While pop-up alerts about updates can appear at inconvenient times, postponing or outright skipping them leaves your system exposed. Many people also ignore updates because they prefer to stick with a version they’re already familiar with, not wanting to learn something new. However, convenience often comes at the cost of security in this scenario.
These updates are specifically designed to fix bugs and close security loopholes that have been identified since the last release. When you miss these crucial updates, you inadvertently leave potential entry points open for hackers to obtain your information or introduce malware. This applies not only to your operating system but also to all your applications. Therefore, turning on automatic updates for your operating system and key programs like your browser and anti-virus software is a practical and essential action step to maintain your digital defenses.
Read more about: Unmasking the True Cost: 12 Hidden Expenses Dealerships Won’t Tell You About Electric Vehicles

4. **Storing Excessive Data**One often overlooked digital privacy mistake is simply accumulating too much data on your devices. The more data you store, especially sensitive information, the more likely you are to become a target for hackers. Each piece of data, in essence, can open a new potential entry point for malicious behavior or provide more material for attackers to exploit.
Think of it this way: every document, photo, old email, or unused application contributes to your digital footprint on that device. If a hacker manages to breach your system, the sheer volume of data makes it easier for them to locate and access sensitive information. It increases the potential reward for their efforts, making your device a more attractive target.
This isn’t to say you shouldn’t store important files, but rather that you should be mindful of what you retain and where. Regularly auditing your stored data and deleting anything unnecessary or obsolete can significantly reduce your risk exposure. Less data means fewer potential entry points and less sensitive information to fall into the wrong hands should a breach occur.
Read more about: Reclaiming Your Attention: A Practical Guide to Breaking Free from the Endless Scroll of Social Media
5. **Neglecting Regular Full System Scans**Even with the most careful online habits, it’s remarkably easy to inadvertently pick up malware or other unwanted software while browsing the internet. Websites can be compromised, malicious ads can be clicked by accident, and drive-by downloads can occur without your explicit knowledge. This makes neglecting regular full system scans a critical digital privacy mistake that leaves your defenses weak.
Running regular, comprehensive system scans is an essential practice to catch and neutralize these threats before they can cause significant damage. These scans delve deep into your system, identifying and quarantining any malicious software that might have slipped through your initial defenses. Without them, malware could reside on your device undetected for extended periods, silently compromising your data and privacy.
The recommendation is to make it a habit to scan your devices at least once each week. This consistent approach ensures that any new threats are identified promptly, minimizing their potential impact. Think of it as a regular health check-up for your digital life; it’s a proactive measure that prevents small issues from escalating into major privacy catastrophes. Consistent vigilance through scanning is a cornerstone of effective digital self-protection.
Read more about: Protect Your Engine: 14 Critical Habits That Will Destroy Your Car’s Lifespan

6. **Mishandling Sensitive Data**Beyond the general act of storing data, the specific ways in which you handle sensitive information can also create significant privacy vulnerabilities. Many people, whether due to negligence or a simple lack of awareness, mishandle data without realizing how easily a hacker could find or exploit it. Understanding the inherent value of personal data is paramount to protecting it effectively.
There are several common ways individuals inadvertently mishandle data that hackers can capitalize on. These include mistakenly deleting files that contain sensitive information without properly wiping them, or removing files without truly understanding their contents. Sending emails to the wrong recipient, even within a trusted organization, can expose private data instantly. Furthermore, mistakenly changing information within a document and then saving or sharing it, or sharing sensitive data through insecure channels, all contribute to increased risk.
For truly sensitive conversations or data transfers, it is critical to employ secure methods. The context highlights that using an end-to-end encrypted messaging app, such as Signal, is far more secure than standard text messages or many common chat applications. Such apps ensure that only the sender and intended recipient can read the messages, preventing interception. Additionally, utilizing features like disappearing messages ensures that private chats vanish after they have been read, further reducing the lingering digital footprint of sensitive information.
Read more about: Voice Assistants: Navigating the Balance Between Convenience and Data Security
7. **Turning Your Firewall Off**Leaving your firewall disabled is a straightforward yet incredibly dangerous digital privacy mistake, effectively rolling out the red carpet for hackers. A firewall acts as a crucial barrier between your computer and the internet, monitoring incoming and outgoing network traffic and blocking unauthorized access attempts. If this essential defense mechanism isn’t active, your system becomes far more susceptible to malicious data and invasive attacks.
Without a functioning firewall, you run a significantly higher risk of unauthorized individuals gaining access to your system and, consequently, your data. Malicious programs can enter more easily, and your sensitive information can be exfiltrated without your knowledge. It’s like leaving the front door of your house wide open in a bustling city; you’re inviting trouble.
It’s a good practice to periodically double-check your firewall settings to ensure it hasn’t been accidentally turned off or inadvertently disabled by another program. While some users might turn it off temporarily for specific tasks or troubleshooting, forgetting to re-enable it can have dire consequences. Keeping your firewall consistently active is a foundational element of maintaining strong digital privacy and a secure computing environment.
Read more about: The Essential Guide to Building an Unbreakable Home Wi-Fi Network: 14 Steps to Digital Peace of Mind
8. **Sharing User Accounts**It might seem harmless to let a friend or family member use your computer. However, a significant digital privacy mistake arises when you allow others to use *your* specific user account. Your account is tied to all your personal settings, saved passwords, browser history, and potentially sensitive documents, making it a gateway to your digital life.
When someone else operates under your logged-in profile, they gain access to a treasure trove of your digital information. Even with the best intentions, they could inadvertently stumble upon private information, accidentally change critical settings, or even download something malicious that compromises your account and data. This oversight, though often stemming from a desire to be helpful, significantly expands the surface area for potential privacy breaches.
The smart, user-centric approach is to establish guest profiles on your devices. Most operating systems, whether for computers or mobile devices, offer this functionality. A guest profile creates a separate, sandboxed environment that prevents access to your personal files and applications, ensuring that any activity performed by another user does not impact your primary account’s security or privacy. This simple, proactive step ensures your personal information remains segmented and secure.
Read more about: Inside the Carter Clan’s Fortress: The Unseen Strategies Protecting Beyoncé and Jay-Z’s Children from the Relentless Spotlight

9. **Holding Sensitive Data on Your Hard Drive Without Encrypting It**Our hard drives often act as digital vaults containing everything from personal photos and financial documents to work files. Yet, a common and dangerous digital privacy mistake is storing sensitive information on these drives without encryption. Without it, your private data is essentially sitting in plain text, accessible to anyone who gains unauthorized physical or digital access to your device.
Consider the risk if you lose your laptop or it’s stolen. If your hard drive isn’t encrypted, a malicious actor could easily remove the drive and access every piece of information stored on it. This isn’t just an inconvenience; it can lead to identity theft, financial fraud, or the exposure of highly personal details. Unencrypted data is also more vulnerable to certain types of cyberattacks, amplifying the risk.
Encrypting your hard drive adds a vital layer of security by scrambling your data, rendering it unreadable without a specific decryption key or password. Modern operating systems often come with built-in encryption tools, such as BitLocker for Windows or FileVault for macOS. Enabling these features requires you to set a strong password, which becomes essential for unlocking and accessing your encrypted data. This indispensable step protects against both physical theft and sophisticated digital intrusions.

10. **Using Unprotected Public Wi-Fi**The appeal of free Wi-Fi at coffee shops or airports is strong, but connecting to unprotected public Wi-Fi networks is a significant digital privacy mistake. These networks are often unsecured, making them a prime hunting ground for hackers eager to exploit unsuspecting users. Without proper protection, your online activity becomes highly vulnerable to interception.
On an unsecured public network, your data is exposed. A malicious actor could spy on your browsing, intercept login credentials for banking or email, or redirect you to deceptive, malicious websites designed to steal your information. They can also steal files or infect your device with malware, all without your knowledge. Such networks lack the robust security protocols found in private environments, making them easy targets.
The solution is straightforward and highly effective: always use a Virtual Private Network (VPN) when connecting to public Wi-Fi. A VPN encrypts all your internet traffic, creating a secure, private tunnel between your device and the internet. This encryption makes your data unreadable to anyone snooping on the network, effectively shielding your online activities from prying eyes.
When selecting a VPN, choose a reputable provider known for strong security. Free VPNs can often be worse than no VPN at all, potentially selling your data or lacking proper encryption. Services like ProtonVPN or MullvadVPN are reliable options mentioned. Investing in a trusted VPN is a small price for the significant boost in digital privacy and security it provides on public networks.
Read more about: The Smartest Ways to Protect Your Online Privacy in 2025: An Essential Lifehacker’s Guide
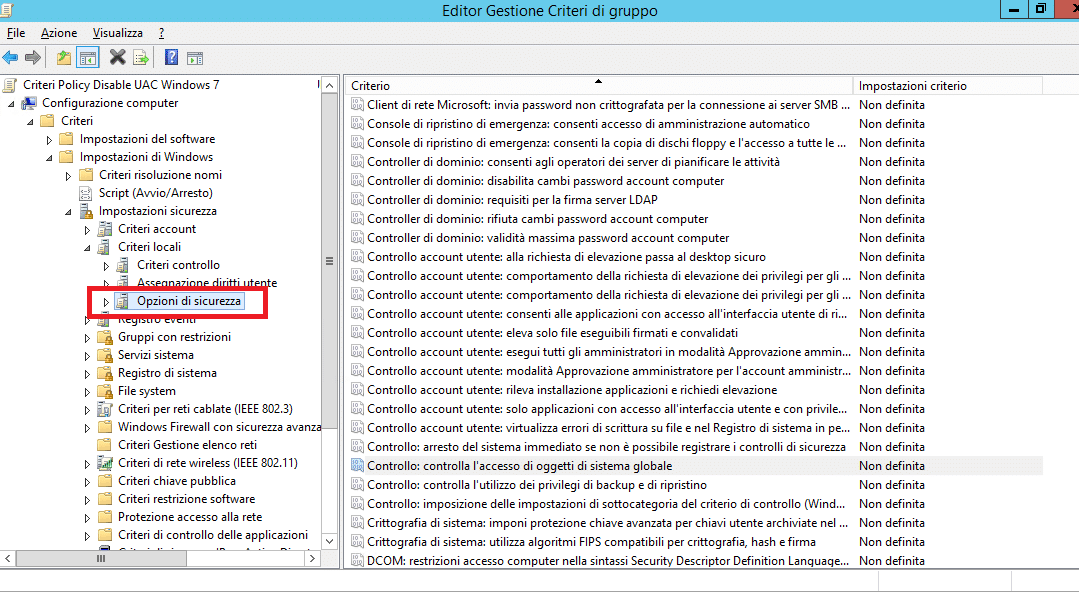
11. **Accidentally Disabling User Account Control (UAC)**User Account Control (UAC) is a vital Windows security feature designed to prevent unauthorized system changes. Accidentally disabling UAC is a digital privacy mistake that can expose your system to considerable risk. Many users might find UAC prompts intrusive, leading them to turn it off, unaware of the critical protection it provides against malicious software and unintended alterations.
UAC operates by limiting programs and system changes from affecting your entire electronic system without explicit permission. When software attempts administrative privileges, UAC prompts you for approval. This step acts as a powerful gatekeeper, ensuring you authorize any significant modifications, whether initiated by an application or potentially malicious software.
If malware infiltrates your device, a functioning UAC is often the first line of defense against its spread. By requiring explicit permission for elevated actions, UAC can stop malicious programs from making widespread changes, installing unwanted software, or accessing sensitive files without your consent. It acts as a crucial barrier, containing potential damage and giving you a chance to intervene.
Leaving UAC enabled at its recommended settings is a cornerstone of maintaining a secure Windows environment. While its prompts may occasionally interrupt workflow, the protection it offers against malware and unauthorized system modifications is invaluable for safeguarding your digital privacy.

12. **Accepting Requests to Share Your Location**In our app-driven world, prompts to share GPS location are common. While convenient, indiscriminately accepting these requests is a significant digital privacy mistake. Each time you grant an app location access, you potentially expose yourself to illegal tracking and create a detailed digital trail of your movements.
Hackers and malicious entities can exploit shared location data. Beyond tracking, this information can deduce routines, identify home/work addresses, and even reveal when you’re away. Such insights are invaluable to criminals for targeted advertising, physical stalking, or planning burglaries. Many apps collect this data in the background, continuously broadcasting your location.
To mitigate this, be highly selective about which apps get location access. Ask if an app truly *needs* precise GPS, or if “Allow While Using App” or “Ask Next Time” options suffice. Review and adjust location permissions for all apps on your devices. Delete unused apps with location access and disable geotagging on your phone’s camera. Being proactive about location sharing significantly reduces exposure to unwanted tracking, safeguarding your physical privacy.
Read more about: Beyond the Dashboard: Unmasking the Shocking Data Collection Habits of Your Connected Car
13. **Clicking Links or Opening Attachments in Emails**The internet is rife with phishing attempts and malicious emails designed to trick you. A common and often devastating mistake is clicking suspicious links or opening attachments without proper verification. These deceptive emails can look incredibly legitimate, making it easy for even tech-savvy individuals to fall victim.
Attackers are masters of social engineering, crafting emails mimicking trusted organizations or colleagues. Embedded links often lead to fake websites identical to genuine login pages, where users unknowingly hand over credentials. Attachments can contain ransomware or malware that, once opened, infects your system, steals data, or encrypts files for ransom.
The golden rule is extreme caution. Never click a link or open an attachment unless absolutely certain of the sender’s identity and you expect the content. Even from a known contact, be wary if the email seems unusual, urgent, or too good to be true. Independently verify the sender through a separate channel, like a phone call, rather than replying to the suspicious email. For online services, type the URL directly into your browser to ensure you’re accessing the genuine site, a cornerstone of protecting your information.
14. **Oversharing on Social Media**Social media platforms are for sharing, but a critical digital privacy mistake is oversharing personal details. While tempting to post about every life aspect, this can inadvertently provide malicious actors with information that compromises your security and even physical safety.
Consider seemingly innocent posts: tagging your exact location, detailing evening plans, or announcing a vacation. These details can be pieced together by online creeps or criminals to profile your routines, whereabouts, and when your home is unoccupied. You’re inadvertently making it too easy for them.
Certain information should *never* be posted on social media. This includes your full birthdate (key for identity theft), your home address, and your phone number. Resist posting vacation plans in real-time; wait until you’re back home to share pictures. Any confidential work-related information must also be strictly avoided.
Adopt a “less is more” mindset for personal details online. Review privacy settings to limit who sees your posts and information. By being judicious, you significantly reduce the risk of becoming a target for stalking, identity theft, or burglary. Your digital privacy on social platforms directly depends on the caution you exercise.
Read more about: Beyond the Red Carpet: Inside Ryan Gosling’s Guarded World and the Unwavering Commitment to His Family’s Privacy
15. **Posting Pictures with Metadata**That innocent selfie or scenic photo you post online could reveal more than you intend, making “posting pictures with metadata” a significant digital privacy mistake. Most digital cameras, especially smartphones, embed detailed information into image files, known as metadata or EXIF data. This data is often overlooked but can inadvertently expose sensitive personal details.
This embedded metadata can reveal a surprising amount of information. Crucially, it often includes the exact GPS coordinates (location) where the photo was taken, along with the precise date and time. It might also contain details about the device used and sometimes even the name of the photographer. This means a picture of your home, workplace, or even a sensitive document could unwittingly betray its precise location.
For example, a picture of your new car in your driveway could contain your home’s precise location. A photo from your office desk might reveal proprietary information if it’s visible in the background and the metadata pinpoints the office location. These seemingly small details, when aggregated, can create a comprehensive blueprint of your life and surroundings, ripe for exploitation.
Before posting any photos online, it is highly recommended to strip out this sensitive metadata. Tools like ImageOptim for Mac or EXIF Purge for Windows can accomplish this. Proactively, disable geotagging on your phone’s camera settings to prevent location data from being recorded initially. This ensures your snapshots don’t inadvertently broadcast your private details to the wider internet.
We’ve journeyed through 15 critical digital privacy mistakes, each revealing a potential vulnerability in our interconnected lives. From foundational errors like weak passwords and neglecting updates, to the nuanced missteps of oversharing on social media or mishandling photo metadata, the online security landscape is complex. While threats are real and ever-evolving, awareness is your most powerful tool. By understanding these common pitfalls and actively implementing the practical, actionable advice we’ve covered, you can significantly fortify your digital defenses. Protecting your privacy isn’t about becoming a tech expert overnight; it’s about making informed choices, adopting vigilant habits, and recognizing that every online interaction carries implications for your personal data. Take these insights to heart, apply them diligently, and navigate the digital world with confidence, knowing you’re doing everything you can to keep your personal information secure.






