
Electronic warfare is evolving swiftly in modern conflicts, posing intricate challenges that transcend military operations. Recent observations from regions such as the Middle East and Ukraine indicate the utilization of advanced techniques targeting Global Navigation Satellite Systems (GNSS), on which modern navigation, both military and civilian, is heavily dependent. These techniques, especially jamming and spoofing, are not only affecting the trajectories of guided munitions but are also increasingly disrupting daily life and commerce.
Traditionally, GNSS spoofing entailed making a device believe that it had instantaneously relocated to a different, fixed location by overpowering legitimate satellite signals with a stronger, false one. This approach, while effective, might exhibit a pattern detectable by sophisticated military systems designed for guided munitions that follow specific trajectories. As conflicts progress, so do the countermeasures and the tactics employed to counteract them.
Amid these evolving electronic warfare scenarios, new patterns are being observed, which signify a substantial leap in sophistication. These advancements underscore a continuous, dynamic interaction between emerging offensive and defensive capabilities in the electronic realm, driven by the requirements of contemporary battlefields. The ramifications of these evolving techniques are extensive, encompassing military strategy, international relations, and global civilian safety and commerce.

1. **Discovery of an ‘Exotic New’ Spoofing Pattern** A technology expert, Sean Gorman, the co-founder and Chief Executive Officer of Zephyr.xys, a company dedicated to enhancing mobile location services, has reported that his team may have encountered what he refers to as an “exotic new” hack. This observation was made during the ongoing conflict between Iran and Israel, during which both countries have engaged in barrages of missiles and drones. The context of this discovery is of paramount importance, as it emerged from a war that commenced in mid – June following Israeli strikes on various positions.
GNSS data is of fundamental significance to the navigation of numerous missile systems worldwide, including those employed by Iran to locate their targets. Standard spoofing entails broadcasting a radio signal that is stronger than satellite signals, forcing a device to process false location data. Typically, this fabricated data presents itself to the receiving device as an instantaneous relocation to a pre – determined false point, a pattern that is potentially detectable or predictable.
However, Sean Gorman believes that the behavior observed by his team represents a highly sophisticated variant. This advanced spoofing technique is designed to imitate the natural, arcing flight paths that are characteristic of missiles and other guided munitions. By replicating such a trajectory with synthetic data, the objective is to divert these systems to safer locations without immediately alerting them to the deception.
Military equipment: List of Ig Nobel Prize winners
Categories: All articles with dead external links, All articles with unsourced statements, Articles with dead external links from June 2024, Articles with permanently dead external links, Articles with short description, Articles with unsourced statements from April 2024, Articles with unsourced statements from January 2025, CS1: long volume value, CS1: unfit URL, CS1 Italian-language sources (it), CS1 Russian-language sources (ru), CS1 errors: missing periodical, Commons category link from Wikidata, Ig Nobel Prize, Lists of award winners, Science and technology award winners, Short description is different from Wikidata, Use dmy dates from November 2019, Webarchive template wayback links
Summary: A parody of the Nobel Prizes, the Ig Nobel Prizes are awarded each year in mid-September, around the time the recipients of the genuine Nobel Prizes are announced, for ten achievements that “first make people laugh, and then make them think”. Commenting on the 2006 awards, Marc Abrahams, editor of Annals of Improbable Research and co-sponsor of the awards, said that “[t]he prizes are intended to celebrate the unusual, honor the imaginative, and spur people’s interest in science, medicine, and technology”. All prizes are awarded for real achievements, except for three in 1991 and one in 1994, due to an erroneous press release.
Get more information about: List of Ig Nobel Prize winners
2. **Mechanism: Mimicking Arcing Trajectories to Deceive** This newly developed sophisticated spoof, as described by Sean Gorman, diverges from conventional spoofing methods by generating a synthetic position that follows a curved trajectory. Unlike typical spoofing, which results in the device being fixed at a teleported location, this advanced technique is designed to simulate realistic movement patterns, specifically the arcing paths that guided munitions follow during flight. This subtle approach renders the deception more difficult to detect.
The crux of this sophisticated method lies in its capacity to deceive a guided munition into believing that it is still on its pre – programmed trajectory, even while it is being fed false navigation data. Sean explained, “If you experience a sudden, large – scale teleportation and the location is fixed, that would present a pattern vastly different from that of a guided munition on a trajectory.” He emphasized the objective: “You want that munition to think it is still on the trajectory.”
By imitating the expected flight path, the spoofing operator can effectively ‘guide’ the munition along a different, synthetic path. Sean noted, “It continues along the path that the spoof operator is guiding it.” This seamless redirection is intended to be imperceptible to the munition’s internal systems. As Sean put it, “They do not realize they are being spoofed because they are continuing to follow a trajectory. That would deceive a drone.”
Military equipment: MH-60 Jayhawk
Manufacturer: Sikorsky
Categories: Coast Guard Aircraft, Coast Guard Equipment, Coast Guard Helicopters, Helicopters, Military Aircraft, Special Mission Aircraft
Get more information about: MH-60 Jayhawk
3. **Detection Method: Observation via Mobile Phone Data** The detection of this peculiar signal pattern was achieved through an unlikely yet effective medium: a mobile phone equipped with Zephyr software. Sean Gorman’s team commenced tracking spoofing and jamming activities during their volunteer work in Ukraine, discovering that phones loaded with their software were highly proficient in identifying these types of electronic attacks. This prompted further research, which was supported by an American government grant.
As part of this research endeavor, phones with Zephyr’s app installed were distributed globally to regions known for frequent electronic interference. One such device was dispatched to Haifa, a city in northern Israel that, like many others in the country, had been subjected to attacks from Iranian missiles. It was via the data reported by this particular mobile phone located in Haifa that Gorman and his team detected the unique signal.
Sean elaborated on the crucial observation to MailOnline: “The phone was located in Haifa, and the positions that the phones were reporting were inaccurately positioned in the ocean.” He emphasized the deviation from typical patterns: “And instead of being teleported to a fixed location, we observed this arc.” This single measurement from one phone, which displayed a synthetically generated position that curved, represented, according to Sean, “a new behavior or pattern that we had not previously encountered,” indicating the presence of a potentially new type of ‘push spoofer’.
Military equipment: Mobile security
Categories: All articles needing additional references, All articles with failed verification, All articles with incomplete citations, All articles with specifically marked weasel-worded phrases, All articles with unsourced statements, All articles with vague or ambiguous time, Articles needing additional references from November 2022, Articles needing additional references from October 2023, Articles with failed verification from October 2023, Articles with incomplete citations from March 2023, Articles with short description, Articles with specifically marked weasel-worded phrases from March 2023, Articles with unsourced statements from April 2012, Articles with unsourced statements from February 2017, Articles with unsourced statements from March 2023, Articles with unsourced statements from October 2023, CS1 French-language sources (fr), Mobile security, Short description is different from Wikidata, Vague or ambiguous time from March 2023, Wikipedia articles needing clarification from October 2023
Summary: Mobile security, or mobile device security, is the protection of smartphones, tablets, and laptops from threats associated with wireless computing. It has become increasingly important in mobile computing. The security of personal and business information now stored on smartphones is of particular concern.
Increasingly, users and businesses use smartphones not only to communicate, but also to plan and organize their work and private life. Within companies, these technologies are causing profound changes in the organization of information systems and have therefore become the source of new risks. Indeed, smartphones collect and compile an increasing amount of sensitive information to which access must be controlled to protect the privacy of the user and the intellectual property of the company.
The majority of attacks are aimed at smartphones. These attacks take advantage of vulnerabilities discovered in smartphones that can result from different modes of communication, including Short Message Service (SMS, text messaging), Multimedia Messaging Service (MMS), wireless connections, Bluetooth, and GSM, the de facto international standard for mobile communications. Smartphone operating systems or browsers are another weakness. Some malware makes use of the common user’s limited knowledge. Only 2.1% of users reported having first-hand contact with mobile malware, according to a 2008 McAfee study, which found that 11.6% of users had heard of someone else being harmed by the problem. Yet, it is predicted that this number will rise. As of December 2023, there were about 5.4 million global mobile cyberattacks per month. This is a 147% increase from the previous year.
Security countermeasures are being developed and applied to smartphones, from security best practices in software to the dissemination of information to end users. Countermeasures can be implemented at all levels, including operating system development, software design, and user behavior modifications.
Get more information about: Mobile security

4. **Signal Origin and Global EW Development Context** While the exact perpetrator of the hack remains indeterminate based on Sean Gorman’s analysis, the origin of the signal is widely believed to be located within the Middle East region. This context is consistent with the prevailing understanding that electronic warfare capabilities, encompassing sophisticated GNSS manipulation techniques, are being actively developed and refined by multiple nations across the globe.
Sean emphasized that conflicts such as the invasion of Ukraine act as significant catalysts for the evolution of these technologies. He remarked, “There are numerous countries that possess highly skilled technical engineers and expertise in GNSS.” These countries are engaged in an ongoing endeavor to enhance their own electronic warfare capabilities while concurrently developing countermeasures to neutralize those of their adversaries.
This dynamic engenders a perpetual ‘cat-and-mouse game,’ as Sean characterized it, alluding to the interactions between forces in Ukraine and the Middle East. “We observe this phenomenon among the Russians and Ukrainians, who are ceaselessly iterating and attempting to overcome each other’s countermeasures in this type of cat-and-mouse game,” he stated. He further added, “Countries are allocating resources and striving to devise countermeasures and counter-countermeasures so that they can continue to operate effectively in battle scenarios like those unfolding in the Middle East.” This implies that the sophisticated spoofing observed in the Middle East is an integral part of this broader global trend of electronic warfare advancement.
Military equipment: Royal Corps of Signals
UnitName: Royal Corps of Signals
Caption: Cap Badge of the Royal Corps of Signals during the reign of Elizabeth II
Dates: 1920 – present
Allegiance: United Kingdom
Branch: army
Garrison: Blandford Camp,Dorset
Motto: Certa Cito,(Swift and Sure),
March: Begone Dull Care (Quick); HRH The Princess Royal (Slow)
Commander1: Anne, Princess Royal
Commander1Label: Colonel-in-Chief
Commander2: Major-General Mark R. Purves
Commander2Label: Colonel Commandant
Commander3: Paul Griffiths (British Army officer)
Commander3Label: Master of Signals
Commander4: Colonel Nicholas Bruce
Commander4Label: Corps Colonel
IdentificationSymbol: Image:Royal Signals TRF.svg
IdentificationSymbolLabel: Tactical Recognition Flash
Categories: 1920 establishments in the United Kingdom, Articles with short description, British Army, British administrative corps, Commons category link is on Wikidata, Military communications corps, Military units and formations established in 1920, Pages containing London Gazette template with parameter supp set to y, Royal Corps of Signals, Short description is different from Wikidata, Use dmy dates from February 2021, Webarchive template wayback links
Summary: The Royal Corps of Signals (often simply known as the Royal Signals – abbreviated to R SIGNALS) is one of the combat support arms of the British Army. Signals units are among the first into action, providing the battlefield communications and information systems essential to all operations. Royal Signals units provide the full telecommunications infrastructure for the Army wherever they operate in the world. The Corps has its own engineers, logistics experts and systems operators to run radio and area networks in the field. It is responsible for installing, maintaining and operating all types of telecommunications equipment and information systems, providing command support to commanders and their headquarters, and conducting electronic warfare against enemy communications.
Get more information about: Royal Corps of Signals
Read more about: The Shifting Language of Images: Exploring Symbols Whose Meanings Have Transformed Through History
5. **Expanding Impact: Risks to Civilian and Commercial Operations** While sophisticated GNSS spoofing and jamming techniques are primarily developed for military advantage, the increasing competition and deployment of these technologies pose significant risks that extend far beyond the battlefield. These electronic interference tactics exhibit a growing tendency to be employed in ways that can have broader, unintended impacts on civilians and essential commercial activities.
Sean Gorman highlighted recent events that illustrate this expanded impact. Last week, a collision took place near the Strait of Hormuz involving the Frontline tanker Front Eagle and the dark fleet tanker Adalynn. This incident, which caused both oil tankers to come to a standstill after a fire, was preceded by a warning from the UK’s Maritime Trade Operations, which reported “increasing electronic interference” in the Strait of Hormuz in the days leading up to the collision.
Sean noted that this event suggests a growing readiness among warring parties to utilize spoofing and jamming in ways that can affect global commerce and supply chains. He remarked, “We are increasingly witnessing this phenomenon occur across the globe, causing issues with global commerce, supply chains, and aviation.” This indicates that the risks are not limited to military engagements but are becoming more prevalent in daily civilian life and critical infrastructure operations.
Military equipment: 2025 India–Pakistan conflict
Categories: 2020s in Jammu and Kashmir, 2025 airstrikes, 2025 in international relations, 2025 military operations, 21st century in Azad Kashmir, Airstrikes conducted by India, Airstrikes conducted by Pakistan, All articles lacking reliable references, All articles with minor POV problems, All pages needing factual verification, Articles lacking reliable references from May 2025, Articles with minor POV problems from May 2025, Articles with short description, Attacks in Asia in 2025, Attacks on military headquarters, Attacks on military installations in 2025, Attacks on military installations in Jammu and Kashmir, CS1: unfit URL, CS1 Arabic-language sources (ar), CS1 Bengali-language sources (bn), CS1 Marathi-language sources (mr), CS1 Swiss High German-language sources (de-ch), CS1 Urdu-language sources (ur), May 2025 in India, May 2025 in Pakistan, Military operations of the Kashmir conflict, Short description is different from Wikidata, Use dmy dates from June 2025, Wikipedia articles needing factual verification from June 2025, Wikipedia articles needing factual verification from May 2025, Wikipedia extended-confirmed-protected pages
Summary: The 2025 India–Pakistan conflict was a brief armed conflict between India and Pakistan that began on 7 May 2025, after India launched missile strikes on Pakistan, in a military campaign codenamed Operation Sindoor. India said that the operation was in response to the Pahalgam terrorist attack in Indian-administered Jammu and Kashmir on 22 April 2025 in which 26 civilians were killed. India accused Pakistan of supporting cross-border terrorism, which Pakistan denied.
On 7 May, India launched Operation Sindoor with missile strikes on terrorism-related infrastructure facilities of Pakistan-based militant groups Jaish-e-Mohammed and Lashkar-e-Taiba in Pakistan and Pakistan-administered Azad Kashmir, and said that no Pakistani military or civilian facilities were targeted. According to Pakistan, the Indian strikes hit civilian areas, including mosques, and resulted in civilian casualties. Following these strikes, there were border skirmishes and drone strikes between the two countries. Pakistan’s army retaliated on 7 May, by launching a blitz of mortar shells on Jammu, particularly Poonch, killing civilians, and damaging homes and religious sites. This conflict marked the first drone battle between the two nuclear-armed nations.
In the early hours of 10 May, India accused Pakistan of launching missile attacks on Indian air bases including the Sirsa air base while Pakistan accused India of launching attacks on several Pakistan air bases, including Nur Khan air base, Rafiqi air base, and Murid air base. As conflict escalated on 10 May, Pakistan launched its Operation Bunyan-un-Marsoos, in which it said it had targeted several Indian military bases.
After the four-day military conflict, both India and Pakistan announced that a ceasefire had been agreed after a hotline communication between their DGMOs (Directors General of Military Operations) on 10 May 2025. U.S. Vice President JD Vance and Secretary of State Marco Rubio held extensive correspondence with both Indian and Pakistani officials during the negotiations. The ceasefire has been holding with resumed commercial flights and normalcy reported from both countries.
Get more information about: 2025 India–Pakistan conflict
6. **Jamming vs. Spoofing: Prevalence and Detection Challenges** The realm of GNSS interference encompasses several techniques, with jamming and spoofing being the most prominent. Jamming involves overwhelming legitimate GNSS signals with high-power radio noise, rendering it impossible for a receiver to lock onto the satellites and determine its position. Spoofing, as discussed, involves broadcasting counterfeit GNSS signals intended to deceive a receiver into calculating a false location.
Sean Gorman observed that both jamming and spoofing are prevalent forms of electronic interference. However, he emphasized a key distinction in their observed frequency and ease of detection. “Jamming and spoofing are both prevalent, though we observe spoofing less frequently and it is slightly more difficult to detect than jamming,” he declared. The direct disruption of the signal by jamming is often more immediately noticeable to a device or user than the subtle deception employed by spoofing.
Despite the differences in frequency and detection difficulty, Sean underscored that both techniques pose substantial risks to non-military operations. “So, while it was intriguing to witness spoofing activity, both techniques pose risks to civilian and commercial operations.” The potential for collisions in both aviation and maritime contexts is a particular concern, arising from navigation systems receiving either no data (jamming) or incorrect data (spoofing).
Military equipment: Twitter
Name: X
FormerName: Twttr (early 2006),Twitter (2006–2023)
Logo: File:X logo 2023.svg
LogoCaption: Logo used since July 2023.
Screenshot: Screen of X (Twitter).png
Caption: X homepage visited while logged out in CURRENTMONTHNAME CURRENTYEAR
WebsiteType: Social networking service
NativeClients: World Wide Web,Android (operating system),iOS,iPadOS,Fire OS
Language: Multilingual
Foundation: [object Object]
Headquarters: Bastrop, Texas
AreaServed: Censorship of Twitter
Founder: class=nowrap,Jack Dorsey,Noah Glass,Biz Stone,Evan Williams (Internet entrepreneur)
Chairman: Elon Musk
Owner: Odeo,Obvious Corporation,Twitter, Inc.,X Corp.
Url: https://x.com/|x.com
Registration: Required
LaunchDate: [object Object]
CurrentStatus: Active
ContentLicense: Proprietary software
ProgrammingLanguage: Scala (programming language),Java (programming language),Ruby (programming language),JavaScript,Python (programming language)
Categories: 2006 establishments in California, 2006 in San Francisco, All Wikipedia articles in need of updating, All Wikipedia articles needing clarification, All Wikipedia articles written in American English, All articles containing potentially dated statements, All articles with unsourced statements, All articles with vague or ambiguous time, All pages needing factual verification, American social networking mobile apps, American social networking websites, Android (operating system) software, Articles containing Japanese-language text, Articles containing overly long summaries, Articles containing potentially dated statements from 2013, Articles containing potentially dated statements from 2017, Articles containing potentially dated statements from 2019, Articles containing potentially dated statements from 2022, Articles containing potentially dated statements from February 2025, Articles containing potentially dated statements from May 2024, Articles containing potentially dated statements from May 2025, Articles with excerpts, Articles with short description, Articles with unsourced statements from November 2024, CS1 French-language sources (fr), CS1 German-language sources (de), CS1 Italian-language sources (it), CS1 maint: DOI inactive as of July 2025, Elon Musk, IOS software, Internet properties established in 2006, MacOS software, Microblogging services, Multilingual websites, Pages using Sister project links with hidden wikidata, Pages using Sister project links with wikidata mismatch, Pages with login required references or sources, Proprietary cross-platform software, Real-time web, Short description is different from Wikidata, Text messaging, Tor onion services, Twitter, Universal Windows Platform apps, Use American English from June 2025, Use mdy dates from June 2025, Vague or ambiguous time from April 2024, WatchOS software, Webarchive template wayback links, Wikipedia articles in need of updating from October 2022, Wikipedia articles needing clarification from July 2020, Wikipedia articles needing factual verification from August 2024, Wikipedia indefinitely move-protected pages, Wikipedia indefinitely semi-protected pages
Summary: Twitter, officially known as X since 2023, is an American microblogging and social networking service. It is one of the world’s largest social media platforms and one of the most-visited websites. Users can share short text messages, images, and videos in short posts commonly known as “tweets” (officially “posts”) and like other users’ content. The platform also includes direct messaging, video and audio calling, bookmarks, lists, communities, a chatbot (Grok), job search, and Spaces, a social audio feature. Users can vote on context added by approved users using the Community Notes feature.
Twitter was created in March 2006 by Jack Dorsey, Noah Glass, Biz Stone, and Evan Williams, and was launched in July of that year. Twitter grew quickly; by 2012 more than 100 million users produced 340 million daily tweets. Twitter, Inc., was based in San Francisco, California, and had more than 25 offices around the world. A signature characteristic of the service initially was that posts were required to be brief. Posts were initially limited to 140 characters, which was changed to 280 characters in 2017. The limitation was removed for subscribed accounts in 2023. 10% of users produce over 80% of tweets. In 2020, it was estimated that approximately 48 million accounts (15% of all accounts) were run by internet bots rather than humans.
The service is owned by the American company X Corp., which was established to succeed the prior owner Twitter, Inc. in March 2023 following the October 2022 acquisition of Twitter by Elon Musk for US$44 billion. Musk stated that his goal with the acquisition was to promote free speech on the platform. Since his acquisition, the platform has been criticized for enabling the increased spread of disinformation and hate speech. Linda Yaccarino succeeded Musk as CEO on June 5, 2023, with Musk remaining as the chairman and the chief technology officer. In July 2023, Musk announced that Twitter would be rebranded to “X” and the bird logo would be retired, a process which was completed by May 2024. Since Musk’s takeover, data from app-tracking firms has shown that global usage of Twitter has declined by approximately 15%, compared to a decline of 5–10% in some other social media sites. The platform has disputed that usage has dropped at all, with Musk claiming without evidence that membership had grown to 600 million users as of a May 2024 tweet.
In March 2025, X Corp. was acquired by xAI, Musk’s artificial intelligence company. The deal, an all-stock transaction, valued X at $33 billion, with a full valuation of $45 billion when factoring in $12 billion in debt. Meanwhile, xAI itself was valued at $80 billion. In July 2025, Linda Yaccarino stepped down from her role as CEO, which was announced just one day after reports of Musk’s artificial intelligence chatbot Grok making antisemitic comments in a post regarding the July 2025 Central Texas floods.
Get more information about: Twitter

7. **Critical Need for Spoofing Detection Technology** Given the escalating utilization of GNSS interference techniques and their expanding influence on civilian and commercial operations, the capability to accurately detect and counteract these threats is becoming increasingly crucial. Sean Gorman specifically underscored the significance of developing technology capable of detecting spoofing, acknowledging its subtlety in comparison to jamming.
He cautioned that the potential for perilous incidents, such as collisions involving aircraft or ships, is a genuine consequence of navigation systems being compromised. “Collisions could pose an issue both from an aviation perspective, as well as a maritime perspective,” Sean declared. This highlights the tangible safety risks that emerge when GNSS signals, on which modern transportation relies, are manipulated or obstructed.
Therefore, Sean concluded that the capacity to detect spoofing is of paramount importance for ensuring civilian safety. He identified this area as necessitating substantial focus and investment in research and development. “That will be a truly significant area of R&D investment and an area where we will require technological capacity from both a civilian and a defence standpoint,” he asserted. The continuous development of sophisticated interference techniques necessitates a corresponding enhancement in defensive capabilities to safeguard vulnerable systems.
Electronic warfare’s scope extends far beyond the direct confrontation between military forces, increasingly impacting civilian populations and critical infrastructure. The practical application and broader impact of Global Navigation Satellite System (GNSS) interference have become stark realities, particularly evident in regions experiencing heightened tensions and conflict. Examining recent events offers a clearer understanding of how these technologies disrupt daily life and pose broader challenges.
Since the commencement of the war in Gaza last October, Israel has substantially increased its use of GPS jamming, a tactic aimed at disrupting satellite signals. This intensified jamming has not been restricted to Gaza itself but has also been extended to parts of Lebanon, particularly amid concerns of a potential escalation into a full – scale conflict with Hezbollah. Such measures, while intended to reinforce air defence systems and thwart potential attacks, inherently carry the risk of broader impact.
Reports indicate that Israel also escalated its GPS jamming in the region in the days leading up to Iran’s unprecedented drone and missile attack on April 13. The primary objective of this jamming is defensive, aiming to impede an opponent’s ability to effectively use drones or precision – guided munitions that rely heavily on GPS for accurate targeting. This tactic serves as a countermeasure to reduce the threat posed by guided weaponry, such as those believed to be in Hezbollah’s arsenal.
Military equipment: Spoofing attack
Categories: All articles with failed verification, All articles with unsourced statements, Articles with failed verification from August 2016, Articles with short description, Articles with unsourced statements from December 2021, CS1: long volume value, Computer network security, Short description matches Wikidata, Types of cyberattacks
Summary: In the context of information security, and especially network security, a spoofing attack is a situation in which a person or program successfully identifies as another by falsifying data, to gain an illegitimate advantage.
Get more information about: Spoofing attack
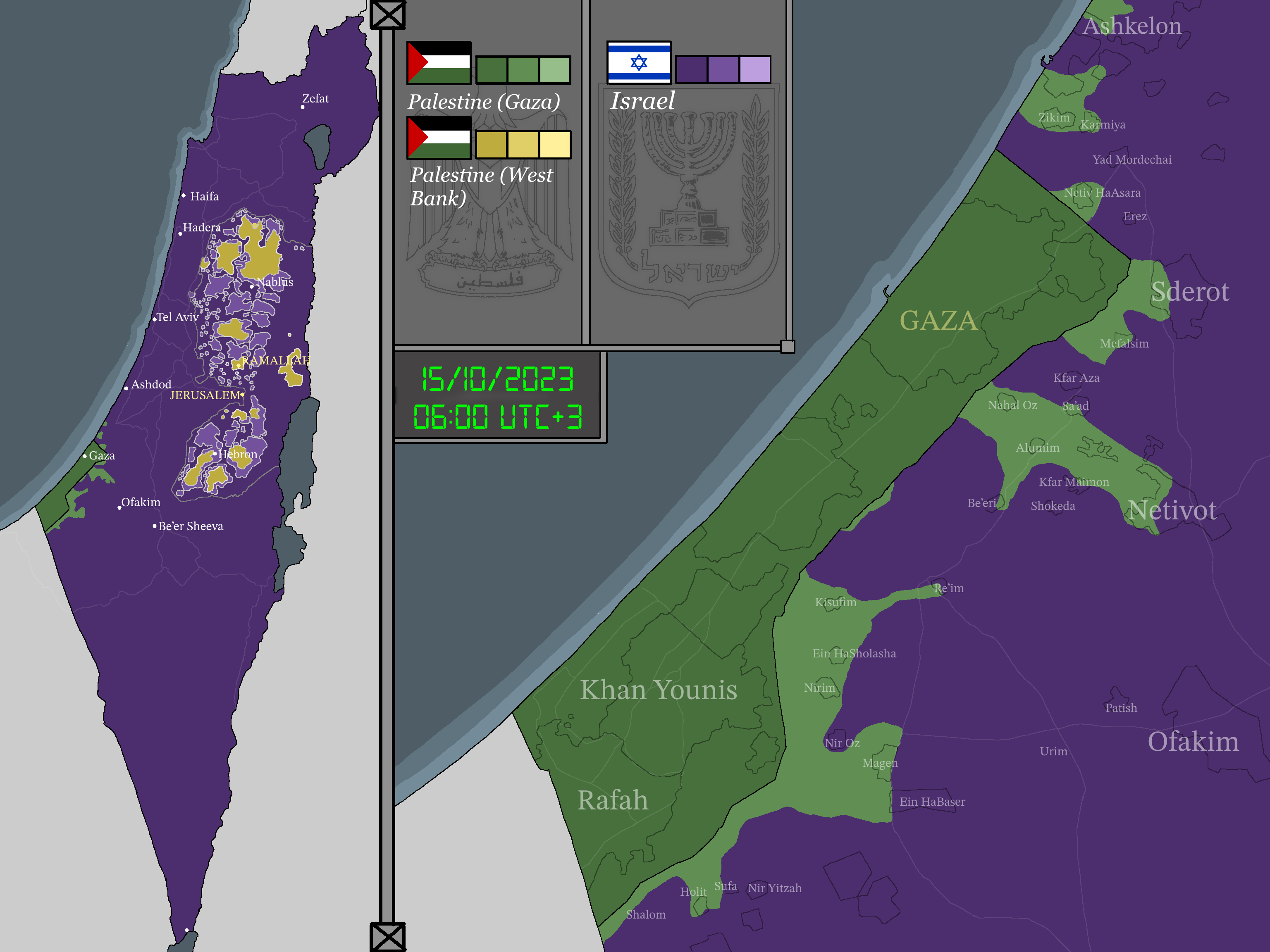
8. **Israel’s Extensive Use of Jamming Since Gaza Conflict Began** Israel has indeed escalated its utilization of GPS jamming since the commencement of the war in Gaza last October, as indicated by security analysts. This electronic countermeasure is being implemented as a defensive capability, particularly against potential attacks from groups such as Hezbollah in Lebanon. By deliberately interfering with GPS signals, the objective is to disrupt the navigation systems of incoming projectiles, thereby making it difficult for them to accurately reach their intended targets.
This intensified jamming has also been extended to parts of Lebanon, in addition to its use in the immediate vicinity of Gaza. The rationale underlying this broader application seems to be connected to concerns about a wider conflict in the region. While effective from a military perspective in potentially thwarting guided missile or drone attacks, this widespread electronic interference inevitably has spill – over effects, posing challenges for civilian navigation and communication systems that rely on the same satellite signals.
Freddy Khoueiry, a global security analyst, observed, “Israel has escalated its utilization of GPS jamming since the commencement of the war in Gaza last October. It has also extended this to parts of Lebanon amid concerns of a full – scale war with Hezbollah.” He also underscored its use prior to Iran’s April 13 strikes. Nicholas Blanford, a senior fellow at the Atlantic Council, commented on the defensive nature, stating, “I believe that the Israelis are employing jamming techniques in a defensive capacity against potential attacks by Hezbollah rather than as a pre – emptive measure before launching any form of attack in Lebanon.”
Military equipment: Gaza war
Group: Casualties of the Gaza war,#tag:ref
Last1: Deutsch
First1: Anthony
Author1Link: Patrick Wintour
Date: Fri Jan 12 2024 00:00:00 GMT-0800 (Pacific Standard Time)
Title: Israel rejects genocide charges, tells World Court it must defend itself
Url: https://www.reuters.com/world/middle-east/israel-counter-genocide-accusations-world-court-2024-01-12/
Work: Reuters
AccessDate: Nova music festival massacre
Last2: Sterling
First2: Toby
Last3: van den Berg
First3: Stephanie
Categories: 2020s conflicts, 2020s in Israel, 2020s in Palestine, 2023 in military history, All Wikipedia articles in need of updating, All Wikipedia articles written in American English, All articles containing potentially dated statements, All articles with failed verification, Articles containing Arabic-language text, Articles containing Hebrew-language text, Articles containing potentially dated statements from July 2025, Articles containing potentially dated statements from June 2025, Articles containing potentially dated statements from May 2025, Articles containing video clips, Articles with Encyclopædia Britannica links, Articles with failed verification from April 2025, Articles with short description, Benjamin Netanyahu, CS1 Arabic-language sources (ar), CS1 French-language sources (fr), CS1 Hebrew-language sources (he), CS1 Portuguese-language sources (pt), CS1 Spanish-language sources (es), CS1 uses Arabic-language script (ar), CS1 uses Hebrew-language script (he), Gaza war, Gaza–Israel conflict, Houthis, Invasions of Israel, Iran–Israel proxy war, Israeli–Palestinian conflict, Middle Eastern crisis (2023–present), Pages using multiple image with auto scaled images, Short description is different from Wikidata, Use American English from October 2023, Use dmy dates from May 2025, Violence in Palestine, Wars involving Iran, Wars involving Israel, Wars involving Palestinians, Webarchive template wayback links, Wikipedia articles in need of updating from April 2025, Wikipedia articles in need of updating from May 2024, Wikipedia extended-confirmed-protected pages
Summary: The Gaza war is an armed conflict in the Gaza Strip and Israel fought since 7 October 2023, as part of the unresolved Israeli–Palestinian and Gaza–Israel conflicts dating back to the 20th century. On 7 October 2023, Hamas-led militant groups launched a surprise attack on Israel, in which 1,195 Israelis and foreign nationals, including 815 civilians, were killed, and 251 taken hostage with the stated goal of forcing Israel to release Palestinian prisoners. Since the start of the Israeli offensive that followed, over 58,000 Palestinians in Gaza have been killed, over half of them women and children, and more than 137,000 injured. A study in the Lancet estimated 64,260 deaths in Gaza due to traumatic injuries by June 2024, while noting a larger potential death toll when “indirect” deaths are included.
The Gaza war follows the wars of 2008–2009, 2012, 2014, and 2021. After clearing militants from its territory, Israel launched a bombing campaign and invaded Gaza on 27 October with the stated objectives of destroying Hamas and freeing the hostages. Israeli forces launched numerous campaigns during the invasion, including the Rafah offensive from May 2024, three battles fought around Khan Yunis, and the siege of North Gaza from October 2024, and have assassinated Hamas leaders inside and outside of Gaza. A temporary ceasefire in November 2023 broke down, and a second ceasefire in January 2025 ended with a surprise attack by Israel in March 2025.
The war has resulted in a humanitarian crisis in Gaza. Israel’s tightened blockade of Gaza cut off basic necessities, causing a severe hunger crisis with a high risk of famine persisting as of May 2025. By early 2025, Israel had caused unprecedented destruction in Gaza and made large parts of it uninhabitable, leveling entire cities and destroying hospitals (including children’s hospitals), agricultural land, religious and cultural landmarks, educational facilities, and cemeteries. Gazan journalists, health workers, aid workers and other members of civil society have been detained, tortured and killed. Nearly all of the strip’s 2.3 million Palestinian population have been forcibly displaced. Over 100,000 Israelis were internally displaced at the height of the conflict. The first day was the deadliest in Israel’s history, and the war is the deadliest for Palestinians in the broader conflict.
Many human rights organizations and scholars of genocide studies and international law say that a genocide is taking place in Gaza, though some dispute this. Experts and human rights organizations have also stated that Israel and Hamas have committed war crimes. A case accusing Israel of committing genocide in Gaza is being reviewed by the International Court of Justice, while the International Criminal Court issued arrest warrants for Benjamin Netanyahu, Yoav Gallant and Mohammed Deif, though Deif’s warrant was withdrawn when he was killed. Torture and sexual violence have been committed by Palestinian militant groups and by Israeli forces.
Flashpoints during the war attracting global attention include the Nova festival massacre, the kidnapping and killing of the Bibas family, the Al-Ahli Arab Hospital explosion, the Flour Massacre, the Tel al-Sultan attack, the World Central Kitchen aid convoy attack, and the killing of five-year-old Hind Rajab. Israel has received extensive military and diplomatic support from the United States, which has vetoed multiple pro-ceasefire resolutions from the UN Security Council. The war has reverberated regionally, with Axis of Resistance groups across several Arab countries and Iran clashing with the United States and Israel. By late 2024, a year of strikes between Israel and Hezbollah led to the Israeli invasion of Lebanon and the ongoing Israeli operations in Syria, as well as contributing to the fall of the Assad regime. The war continues to have significant regional and international repercussions, with large protests worldwide calling for a ceasefire, as well as a surge of antisemitism and anti-Palestinianism.
Get more information about: Gaza war

9. **Resulting Disruption for Civilians in Neighboring Countries Like Jordan** The effects of this heightened electronic interference have been acutely perceived by civilians in neighboring countries, particularly Jordan. Users of location – based applications in that region have reported encountering glitches for several weeks, issues that intensified in the days preceding Iran’s attack on Israel on April 13. These extensive and prolonged disruptions have substantially influenced daily activities that hinge on precise GPS data.
Mohammed Saleh, a Jordanian driver, recounted his experience, mentioning a notable decline in customer bookings on ride – hailing apps such as Uber and Careem. Tourists utilizing these apps discovered that the apps automatically indicated their locations in entirely different cities, at times as distant as Cairo or Beirut, rather than their actual positions in Amman. This compelled many to manually rectify their locations, adding to the inconvenience.
Similarly, tourists attempting to navigate Jordan’s capital on foot reported difficulties with apps like Google Maps. The interference was redirecting their real – time locations, posing a significant obstacle to finding their way around the city. As one visitor from Italy elaborated, this disruption rendered apps like Uber, which are valued for their convenient payment methods and fixed rates, less dependable, prompting a shift back to simply hailing traditional taxis on the street.
Military equipment: Casualties of the Iraq War
Categories: All articles containing potentially dated statements, All articles with dead external links, Articles containing potentially dated statements from February 2009, Articles containing potentially dated statements from October 2011, Articles with dead external links from August 2023, Articles with dead external links from September 2010, Articles with permanently dead external links, Articles with short description, CS1 maint: archived copy as title, George W. Bush administration controversies, Iraq War, Iraq War casualties, Pages containing links to subscription-only content, Pages using military navigation subgroups without wide style, Pages with login required references or sources, Short description is different from Wikidata, Use mdy dates from August 2018, Webarchive template other archives, Webarchive template wayback links, Wikipedia articles needing page number citations from December 2018
Summary: Estimates of the casualties from the Iraq War (beginning with the 2003 invasion of Iraq, and the ensuing occupation and insurgency and civil war) have come in several forms, and those estimates of different types of Iraq War casualties vary greatly.
Estimating war-related deaths poses many challenges. Experts distinguish between population-based studies, which extrapolate from random samples of the population, and body counts, which tally reported deaths and likely significantly underestimate casualties. Population-based studies produce estimates of the number of Iraq War casualties ranging from 151,000 violent deaths as of June 2006 (per the Iraq Family Health Survey) to 1,033,000 excess deaths (per the 2007 Opinion Research Business (ORB) survey). Other survey-based studies covering different time-spans find 461,000 total deaths (over 60% of them violent) as of June 2011 (per PLOS Medicine 2013), and 655,000 total deaths (over 90% of them violent) as of June 2006 (per the 2006 Lancet study). Body counts counted at least 110,600 violent deaths as of April 2009 (Associated Press). The Iraq Body Count project documents 186,901–210,296 violent civilian deaths in their table. All estimates of Iraq War casualties are disputed.
Get more information about: Casualties of the Iraq War

10. **Official Responses and Communications Regarding the Interference** The magnitude of the disruption has spurred official recognition and measures in the affected nations. Haitham Misto, the head of Jordan’s Civil Aviation Regulatory Commission, affirmed that air traffic within the kingdom had been impacted owing to interference with its GPS systems. This necessitated the employment of alternative navigation systems for aircraft landings, underscoring a direct influence on air safety and operations.
Jordanian authorities have officially communicated with their Israeli counterparts regarding the matter. Nedal Alsamara, the director of the Radio Spectrum Management Directorate of Jordan’s Telecommunications Regulatory Commission, declared that Amman had reached out to Israel concerning the issue of GPS spoofing and was anticipating a response. This signifies the cross – border nature of the interference and the diplomatic avenues being utilized to endeavor to resolve it.
Mr. Alsamara also delineated the geographical regions within Jordan that had been most severely affected by the interference with the Global Positioning System. He observed that the western and northern areas of the kingdom were encountering the most substantial disruptions. This corresponds geographically with regions potentially more vulnerable to signals emanating from conflict zones or areas of intensified electronic warfare activity in proximity to Israel’s borders.
Military equipment: Senate Intelligence Committee report on Russian interference in the 2016 United States presidential election
Categories: 116th United States Congress, 2020 documents, 2020 in American politics, All articles to be expanded, Articles to be expanded from August 2020, Articles with short description, CS1 maint: multiple names: authors list, Electoral fraud in the United States, Investigations and assessments of WikiLeaks, Official Reports About Russian interference in the 2016 United States elections or the U.S. Response Thereto, Russian foreign electoral intervention, Short description matches Wikidata, United States documents, Webarchive template wayback links
Summary: The Senate Intelligence Committee report on Russian interference in the United States presidential election, officially titled Report of the Select Committee on Intelligence United States Senate on Russian Active Measures Campaigns and Interference in the 2016 U.S. Election, is the official report in five volumes documenting the findings and conclusions of the United States Senate Intelligence Committee concerning the Russian attack efforts against election infrastructure, Russia’s use of social media to affect the election, the U.S. government’s response to Russian activities, review of the Intelligence Community Assessment, and counterintelligence threats and vulnerabilities. The redacted report is 1,313 pages long. It is divided into five volumes.
The first volume of the report was released on July 25, 2019, and the fifth and last volume was released to the public on August 18, 2020. The Senate Intelligence Committee’s investigation extended more than three years, includes interviews of more than 200 witnesses, and reviews more than one million documents. Marco Rubio, acting committee head, said that “no probe into this matter has been more exhaustive.” On the stature of the report, the Senate Intelligence Committee said the report is “the most comprehensive description to date of Russia’s activities and the threat they posed”.
The Republican-led Senate Intelligence Committee submitted the first part of its five-volume report in July 2019 in which it concluded that the January 2017 Intelligence Community assessment alleging Russian interference was “coherent and well-constructed”. The first volume also concluded that the assessment was “proper”, learning from analysts that there was “no politically motivated pressure to reach specific conclusions”. The final and fifth volume, which was the result of three years of investigations, was released on August 18, 2020, ending one of the United States “highest-profile congressional inquiries.” The Committee report found that the Russian government had engaged in an “extensive campaign” to sabotage the election in favor of Donald Trump, which included assistance from some of Trump’s own advisers.
Like the Mueller report that preceded it, the report does not find a criminal conspiracy between Russia and the Trump campaign, but it does go further than the Mueller report in detailing the many suspicious links between Trump associates and Russian officials and spies. In particular, it describes Paul Manafort as “a grave counterintelligence threat”. According to the report, “some evidence suggests” that Konstantin Kilimnik, to whom Manafort provided polling data, was directly connected to the Russian theft of Clinton-campaign emails. In addition, while Trump’s written testimony in the Mueller report stated that he did not recall speaking with Roger Stone about WikiLeaks, the Senate report concludes that “Trump did, in fact, speak with Stone about WikiLeaks and with members of his Campaign about Stone’s access to WikiLeaks on multiple occasions.”
Get more information about: Senate Intelligence Committee report on Russian interference in the 2016 United States presidential election
11. **Historical Context: Jamming in Previous Conflicts** While the present magnitude and complexity of GNSS interference may seem novel, the utilization of such tactics in conflicts is not without precedent in the region. Israel, for instance, implemented similar electronic warfare measures during its large – scale conflict with Hezbollah in Lebanon in 2006. This historical instance exemplifies a long – established comprehension of the strategic utility of disrupting communication and navigation systems.
Nicholas Blanford recalled the impact of this jamming during the 2006 war. He remarked that Israel disrupted all communication and GPS signals within the immediate border district. The effect was widespread, rendering ordinary cell phones, satellite phones, and GPS signals inoperative in that specific area, effectively isolating it electronically.
This historical context underscores that the current use of jamming is part of an evolving electronic warfare strategy. While the technology and methods may progress, the fundamental principle of denying or manipulating an adversary’s access to essential communication and navigation tools has been a persistent element in recent conflicts in the Middle East.
Military equipment: 2024 Iran–Israel conflict
Conflict: 2024 Iran–Israel conflict
Place: Iran,Iraq,Israel,Syria,West Bank,Lebanon,Jordan,Yemen,Red Sea,Mediterranean Sea,Strait of Hormuz
Border: infobox
TotalWidth: 300
Perrow: 1/1
Footer: Lower Galilee,IDF
Combatant1: United States,United Arab Emirates
Combatant2: Axis of Resistance,[object Object],Ba’athist Syria
Commander1: flagdeco,Israel Katz,Herzi Halevi,Tomer Bar,Donald Trump,Joe Biden,Pete Hegseth,Lloyd Austin,Keir Starmer,John Healey,Rishi Sunak,Grant Shapps,Emmanuel Macron,Michel Barnier,Sébastien Lecornu,Gabriel Attal
Commander2: Ali Khamenei,Masoud Pezeshkian,Ebrahim Raisi,Mohammad-Reza Gharaei Ashtiani,Aziz Nasirzadeh,Mohammad Bagheri (general),Abdolrahim Mousavi,Alireza Sabahifard,Hossein Salami,Amir Ali Hajizadeh,Bashar al-Assad,Ali Mahmoud Abbas,[object Object],Abdul-Malik al-Houthi,Naim Qassem,flagdeco,Ahmad al-Hamidawi,Mohammad al Tamimi,Hadi al-Amiri,flagicon image
Date: Mon Apr 15 2024 00:00:00 GMT-0700 (Pacific Daylight Time)
Partof: Middle Eastern crisis (2023–present)
Units1: armed forces
Units2: flagicon image,General Staff of the Armed Forces of the Islamic Republic of Iran
Url: https://alwatan.sy/archives/385522
Title: الدفاعات السورية تستهدف صواريخ إسرائيلية حاولت التصدي للصواريخ الإيرانية المتجهة للجولان
TransTitle: Syrian defenses targeted Israeli missiles that attempted to confront Iranian missiles heading for the Golan
Language: ar
Work: Al-Watan (Syria)
AccessDate: Thu Apr 18 2024 00:00:00 GMT-0700 (Pacific Daylight Time)
ArchiveDate: Wed Apr 17 2024 00:00:00 GMT-0700 (Pacific Daylight Time)
ArchiveUrl: https://web.archive.org/web/20240417161144/https://alwatan.sy/archives/385522
UrlStatus: Syrian Air Defense Force,Redwan Force
Casualties1: [object Object]
Casualties2: Consulate annex destroyed,170 drones intercepted,Air defense battery and radar system destroyed,Material damage to SAA and Hezbollah military installations
Casualties3: 2 Syrian civilians killed,2 Jordanian civilians injured (by shrapnel)
Result: Iran–Israel war
Categories: 2024 Iran–Israel conflict, All articles with unsourced statements, April 2024 in Iran, April 2024 in Israel, Articles with short description, Articles with unsourced statements from December 2024, CS1 Arabic-language sources (ar), CS1 Hebrew-language sources (he), CS1 Persian-language sources (fa), Conflicts in 2024, Iran–Israel military relations, Iran–Israel proxy war, Middle Eastern crisis (2023–present), October 2024 in Iran, October 2024 in Israel, Pages using multiple image with auto scaled images, Short description matches Wikidata, Use dmy dates from July 2024, Wikipedia extended-confirmed-protected pages
Summary: In 2024, the Iran–Israel proxy conflict escalated to a series of direct confrontations between the two countries in April, July, and October that year. On 1 April, Israel bombed an Iranian consulate complex in Damascus, Syria, killing multiple senior Iranian officials. In response, Iran and its Axis of Resistance allies seized the Israeli-linked ship MSC Aries and launched strikes inside Israel on 13 April. Israel then carried out retaliatory strikes in Iran and Syria on 19 April.
On 31 July, Hamas political leader Ismail Haniyeh was assassinated, in Tehran, Iran. The killing of Haniyeh occurred a few hours after the 2024 Haret Hreik airstrike in Lebanon that assassinated Hezbollah commander Fuad Shukr.
On 1 October, Iran launched a series of missiles at Israel. Israel then carried out more retaliatory strikes against Iran on 26 October. Several months later in June 2025, the Iran–Israel war began, between Iran and the Houthis against Israel and the United States, when Israel launched a surprise attack targeting key Iranian military and nuclear facilities.
Analysts said the April Israeli strikes were limited and signaled a desire to de-escalate. The United States, United Kingdom, France, and Jordan intercepted Iranian drones to defend Israel. Syria shot down some Israeli interceptors, and Iranian proxies in the region also attacked Israel.
Get more information about: 2024 Iran–Israel conflict

12. **Effects on Civilians Within Israel** While designed to safeguard against incoming threats, Israel’s own GPS jamming measures have also yielded unintended consequences for its civilian populace. Reports have surfaced, providing details of instances where Israelis utilizing location – based applications discovered their devices showing incorrect and, at times, alarming locations. This phenomenon elucidates the challenge in precisely circumscribing the impacts of widespread electronic interference.
Nicholas Blanford underscored these reports, noting that Israelis have found themselves geographically located in Beirut as per their GPS apps. This implies a substantial overflow or perhaps a misadjustment of the jamming effects, leading devices to misconstrue signals and compute positions far removed from their actual locations within Israel.
A particularly noteworthy example cited by Blanford pertains to the family location app Life360. Users of this app have reportedly encountered the disconcerting situation of suddenly discovering that their family members, ostensibly situated within Israel, appeared to be on one of Beirut Airport’s runways according to the application’s display. These incidents highlight the real – world implications of electronic warfare on civilian tools and daily life, even within the nation deploying the measures.
Military equipment: Israeli war crimes
Categories: All articles with dead external links, Articles containing video clips, Articles with dead external links from January 2018, Articles with excerpts, Articles with permanently dead external links, Articles with short description, CS1 Arabic-language sources (ar), CS1 French-language sources (fr), CS1 Hebrew-language sources (he), CS1 uses Arabic-language script (ar), Commons category link from Wikidata, Gaza war, Gaza–Israel conflict, Human rights abuses in Israel, Human rights abuses in Palestine, Israel Defense Forces, Israeli war crimes, Pages containing links to subscription-only content, Short description is different from Wikidata, Use dmy dates from November 2024, War crimes committed by country, War crimes in Israel, War crimes in Palestine, War crimes in the Israeli–Palestinian conflict, Webarchive template wayback links, Wikipedia articles needing page number citations from November 2024, Wikipedia extended-confirmed-protected pages
Summary: Israeli war crimes are violations of international criminal law, including war crimes, crimes against humanity and the crime of genocide, which Israeli security forces have committed or been accused of committing since the founding of Israel in 1948. These have included murder, intentional targeting of civilians, killing prisoners of war and surrendered combatants, indiscriminate attacks, collective punishment, starvation, persecution, the use of human shields, sexual violence and rape, torture, pillage, forced transfer, breach of medical neutrality, enforced disappearance, targeting journalists, attacking civilian and protected objects, wanton destruction, incitement to genocide, and genocide.
Israel ratified the Geneva Conventions on 6 July 1951, and on 2 January 2015 the State of Palestine acceded to the Rome Statute, granting the International Criminal Court (ICC) jurisdiction over war crimes committed in the occupied Palestinian territories. Human rights experts argue that actions taken by the Israel Defense Forces during armed conflicts in the occupied Palestinian territories fall under the rubric of war crimes. Special rapporteurs from the United Nations, organizations including Human Rights Watch, Médecins Sans Frontières, Amnesty International, and human rights experts have accused Israel of war crimes.
Since 2006, the United Nations Human Rights Council has mandated several fact finding missions into violations of international law, including war crimes, in the occupied Palestinian territories, and in May 2021 established a permanent, ongoing inquiry. Since 2021, the ICC has had an active investigation into Israeli war crimes committed in the occupied Palestinian territories. Israel has refused to cooperate with the investigations. In December 2023, South Africa invoked the 1948 Genocide Convention and charged Israel with war crimes and acts of genocide committed in the occupied Palestinian territories and Gaza Strip. The case, South Africa v. Israel, was set to be heard at the International Court of Justice (ICJ), and South Africa presented its case to the court on 10 January. In March 2024, the UN special rapporteur on the situation of human rights in the occupied Palestinian territories found there were “reasonable grounds to believe that the threshold indicating the commission” of acts of genocide had been met. In November 2024, the ICC issued arrest warrants for Benjamin Netanyahu and Yoav Gallant for war crimes and crimes against humanity. In December 2024, Amnesty International and Human Rights Watch accused Israel of genocide.
Get more information about: Israeli war crimes

13. **Ukraine’s Effective Spoofing Tactics Against Russian Drones** Moving beyond the Middle East, another notable example of advanced GNSS interference in contemporary conflict arises from Ukraine’s endeavors to counter Russian forces. Ukraine has devised and effectively employed spoofing techniques, not necessarily of the ‘arcing’ variety, but methods capable of deceiving Russian drones, particularly the Shahed (designated by Russia as Geran – 2), into deviating from their intended course or becoming “lost”.
John Hardie, the deputy director of the Russia Program at the Foundation for Defense of Democracies, elucidated the tactic: “Fundamentally, what Ukraine is engaging in is spoofing. That is, they are inputting false GPS targets into these Shahed… drones…” The objective is to make them stray off course without necessarily physically destroying them. This method hinges on subtly manipulating the navigation data that the drone receives.
Hardie expounded on how this operates: “The drones are equipped with a system that is intended to prevent jamming. However, what these techniques are doing is stealthily infiltrating and preventing the drone from realizing that the targets are being altered. It is tricking the drone into heading in the wrong direction.” Data from the Institute for the Study of War (ISW) substantiates the effectiveness of these tactics, revealing a substantial increase in the proportion of Russian drones reported as “lost” due to Ukrainian electronic warfare interference between October and November.
Military equipment: Russian information war against Ukraine
Categories: All articles lacking reliable references, All articles with dead external links, All articles with specifically marked weasel-worded phrases, All articles with style issues, All articles with unsourced statements, Articles containing Russian-language text, Articles lacking reliable references from December 2023, Articles with Russian-language sources (ru), Articles with dead external links from March 2022, Articles with short description, Articles with specifically marked weasel-worded phrases from March 2022, Articles with unsourced statements from December 2023, Articles with unsourced statements from March 2022, CS1 Polish-language sources (pl), CS1 Russian-language sources (ru), CS1 Ukrainian-language sources (uk), CS1 maint: DOI inactive as of July 2025, CS1 uses Russian-language script (ru), CS1 uses Ukrainian-language script (uk), Disinformation in the Russo-Ukrainian War, Information operations and warfare, Interlanguage link template existing link, Propaganda in Russia, Propaganda in the Russo-Ukrainian War, Russian–Ukrainian cyberwarfare, Short description with empty Wikidata description, Ukraine articles needing expert attention, Use dmy dates from May 2025, Webarchive template wayback links, Wikipedia articles needing clarification from March 2022, Wikipedia articles needing clarification from September 2024, Wikipedia articles with style issues from June 2023, Wikipedia extended-confirmed-protected pages
Summary: The Russian information war against Ukraine was articulated by the Russian government as part of the Gerasimov doctrine. They believed that Western governments were instigating color revolutions in former Soviet states which posed a threat to Russia.
The concept of informatsionnaya voyna (Russian: информационная война, lit. ’informational war’) encompasses various strategies, including cyberwarfare, often described as technical defenses against technical attacks in warfare. However, cyberwarfare is just one aspect of Russia’s information war, which may include controlling undersea communications cables, shaping national narratives, manipulating the news cycle, and flooding the information space with Russian bots and trolls. The goal is to achieve strategic victory and exert reflexive control. These efforts were used as part of its disinformation in the Russian invasion of Ukraine.
Due to effective censorship, most media outlets in Russia are government-controlled, allowing Kremlin messaging to successfully sway the citizens of the Russian Federation to support its approach in Ukraine. The Kremlin has denied waging war in Ukraine, claiming it only wants to protect Russian speakers against Ukrainian Nazis. This narrative has been reinforced by Russian television since 2014, giving it an advantage through repetition and familiarity. According to a poll, 58 percent of Russians approved of this perspective between 28 February and 3 March 2022.
Get more information about: Russian information war against Ukraine

14. **Unintended Consequence of Russian Drones Being Redirected into Belarus** One intriguing and perhaps unintended outcome of Ukraine’s efficacious spoofing tactics employed against Russian drones is their diversion into neighboring regions, including Belarus. Ukrainian electronic warfare capabilities are not merely causing drones to go astray or crash but are, in certain cases, directing them towards paths unintended by their operators, occasionally traversing international boundaries.
The Belarusian Hajun Project, an independent monitoring entity, has documented systematic incursions of UAVs into Belarus since July, with the quantity escalating each month. This encompassed a record – high number of 38 Russian Shahed drones entering Belarusian airspace on November 24 and 25. This consistent influx of misguided drones implies a substantial influence from Ukrainian countermeasures.
Belarus has reacted to these airspace violations, even dispatching fighter jets. According to the ISW, this indicates that they were ill – prepared for these incursions, and perhaps Moscow had not fully foreseen or conveyed the potential for this consequence of Ukrainian interference. The situation underscores the unpredictable nature of electronic warfare and its capacity to impact third parties, even allies, as exemplified by an incident where a crashed drone in Kalinkavichy resulted in the authorities detaining the house owner whose camera recorded the event, in what seems to be an endeavor to conceal the issue.
Military equipment: Responses to the COVID-19 pandemic in April 2020
Categories: All articles with unsourced statements, April 2020, Articles tagged with the inline citation overkill template from May 2020, Articles with short description, Articles with unsourced statements from May 2020, CS1 Chinese-language sources (zh), Citation overkill, Incomplete lists from April 2020, Responses to the COVID-19 pandemic in 2020, Short description is different from Wikidata, Timelines of the COVID-19 pandemic in 2020, Use British English from April 2020, Use dmy dates from April 2020, Webarchive template wayback links
Summary: This article documents the chronology of the response to the COVID-19 pandemic in April 2020, which originated in Wuhan, China in December 2019. Some developments may become known or fully understood only in retrospect. Reporting on this pandemic began in December 2019.
The regional global responses are categorized by six WHO offices: Africa, Western Pacific, Eastern Mediterranean, South East Asia, Europes, and Americas.
Get more information about: Responses to the COVID-19 pandemic in April 2020
These examples from the Middle East and Eastern Europe underscore the pervasive and increasingly complex nature of GNSS interference in modern electronic warfare. They illustrate how capabilities developed for military objectives can readily impact civilian life, international relations, and even the airspace of uninvolved nations, highlighting the urgent need for robust defensive technologies and clearer international norms in this rapidly evolving domain.



